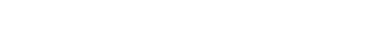Zero to PQC: Start with Cryptographic Inventory
From discovery to remediation,
Discover, inventory, and remediate encryption risks with QryptoCyber’s AI-powered platform.
- AI-Driven Cryptographic Inventory Across External Networks, Internal Assets, Databases, and Code
- Generate and Manage a Complete CBOM (Cryptographic Bill of Materials)
- Build a Strategy and Roadmap to Achieve Post-Quantum Cryptography Resilience
On Premise, Private Cloud, SaaS and Custom Deployments
Encryption Modernization Starts Now
Encryption is in everything we do. Every transaction. Every website. Every database. Every digital interaction.
But no one knows where their encryption is or how to start the process to PQC.
We solve that.
Quantum Computers will break current public key encryption
Quantum computers will break today’s public key encryption. Governments and regulators are already setting 2028 deadlines for critical systems to make the transition. For most enterprises, it will take five to ten years to fully migrate.
QryptoCyber is the first platform purpose-built for complete cryptographic discovery, inventory and remediation strategy at enterprise scale. We deliver a complete cryptographic inventory, turn it into a strategy and roadmap, and connect you to the tools and partners you need — all through our AI-powered platform built for enterprise-scale cryptographic transformation.
Cryptographic AI²
From Inventory to Action
Our Cryptographic Adaptive Inventory Artificial Intelligence transforms your CBOM into a dynamic strategy for remediation, orchestration, and crypto agility.
All through a single AI-powered platform.
We deliver a complete cryptographic inventory. Then we turn it into a strategy, build your remediation roadmap, and connect you to the services and tools needed to execute. All through a single AI-powered platform.
01
CBOM Inventory
Complete five-pillar cryptographic inventory and audit
02
PQC Strategy
Insight-to-action framework driven by your unique environment
03
PQC Roadmap
Sequenced, adaptive remediation plans that evolve with your systems
04
Orchestration & Remediation
Seamlessly connect your CBOM to service providers and PQC tools.
The Importance of a Complete Inventory
A complete inventory enables accurate planning, clear prioritization, and measurable progress. It saves time, money, and frustration in the years ahead.
Partial inventories leave you blind to risk. Without full visibility across all five pillars, including External Network, Internal Network, IT Assets, Databases, and Code, you risk building flawed PQC strategies, wasting resources, and losing trust from leadership.
Our platform secures your encryption and drives your post-quantum readiness.
Prepare for Tomorrow’s Threats Today with a Complete Cryptographic Inventory
QryptoCyber is a cryptographic discovery and inventory platform that finds, categorizes, and analyzes encryption externally, internally, in assets, in databases, and in code. This inventory can be output as a cryptographic bill of materials (CBOM) or as structured data for use in an orchestration platform in a remediation process.
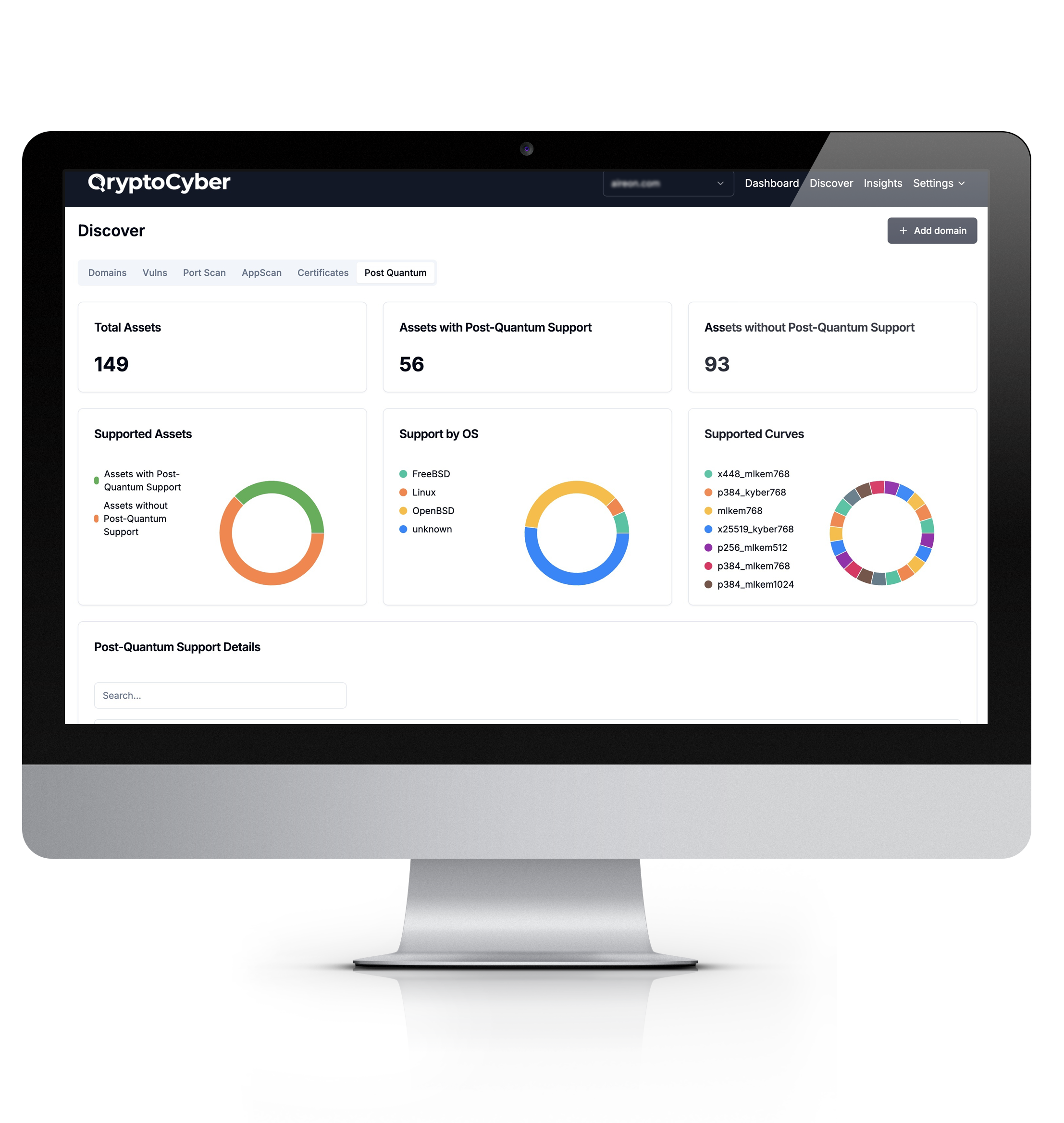
The Five Pillars: Build your roadmap from a complete inventory

The five pillars of cryptographic discovery and inventory form the essential framework for identifying and securing an organization’s cryptographic footprint.
By systematically assessing each area, organizations can prepare for quantum threats, reduce risk exposure, and ensure comprehensive visibility into their cryptographic landscape.
It is crucial to inventory these five pillars as early and as continuously as possible before developing your roadmap for transitioning to PQC standards. Missing just one of these areas could lead to significant budget overruns and leave critical vulnerabilities in undiscovered systems.
Why QryptoCyber
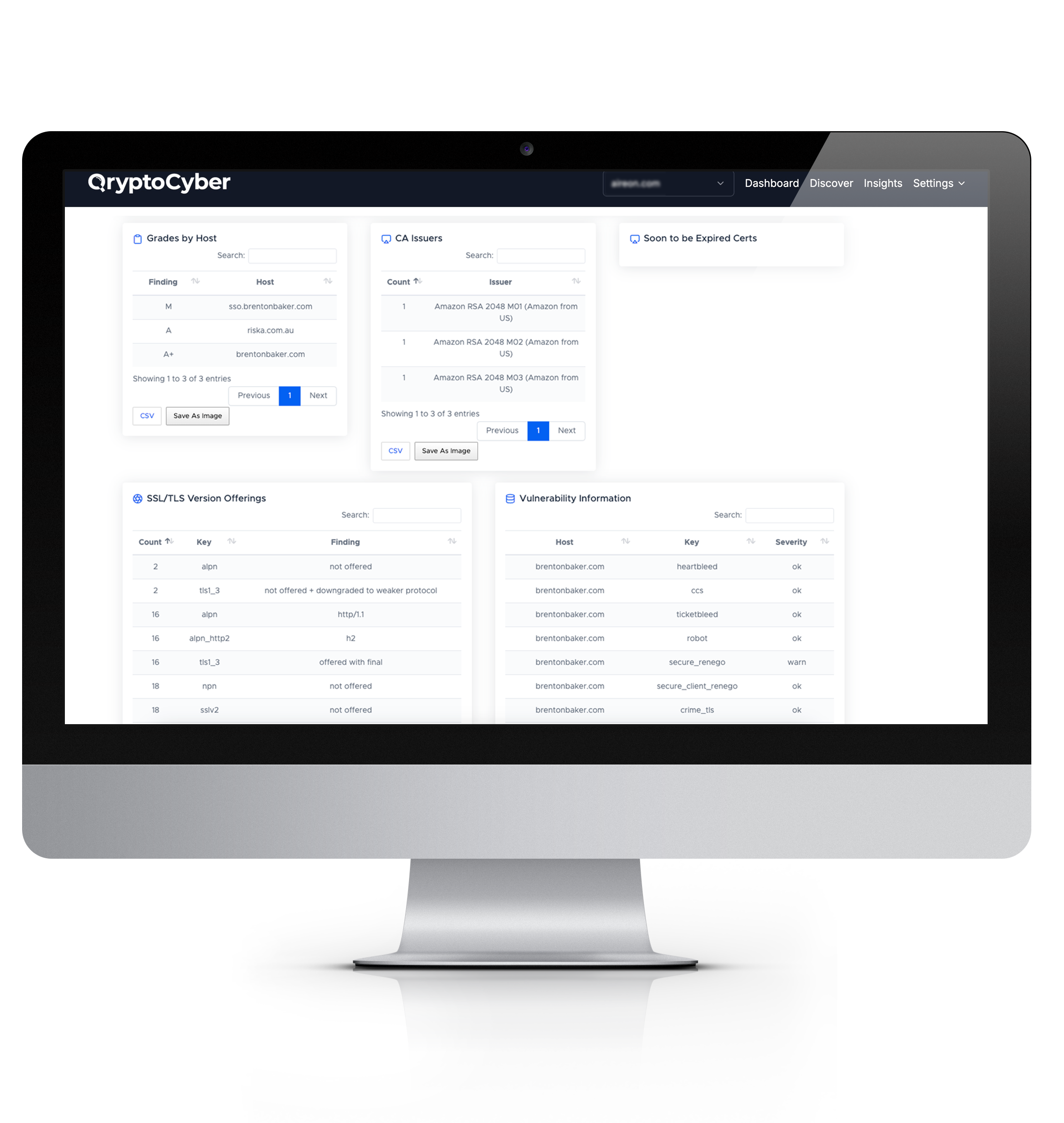
Build Your PQC Strategy & Inventory with QryptoCyber
No Consultants. No Complexity. Just Results.
AI-Powered Information Gathering Strategy
QryptoCyber starts with five foundational prompts — simple, natural-language inputs that tailor the discovery strategy to your specific environment.
01
Integration to Your Environment
We plug into your current infrastructure. Bring your own agents and tools. No installs. No disruption. Faster results. Just faster time to inventory, tailored to your environment.
02
Conduct 5-Pillar Inventory
The five pillars of cryptographic discovery and inventory form the essential framework for identifying and securing an organization’s cryptographic footprint: External Network, Internal Network, IT Assets, Databases and Code.
03
CBOM Generation
Unified CBOM Reporting. Combine scan data from across your toolset into a single Cryptographic Bill of Materials (CBOM). We do the heavy lifting—consolidating, interpreting, and risk ranking cryptographic assets across business units.
04
Cryptographic AI² Strategy
Turn your static inventory or CBOM into action. Cryptographic AI² builds tailored PQC strategies aligned with your compliance, governance, and operational context.
05
Cryptographic AI² Roadmap
Our AI creates sequenced roadmaps that automatically update with changes in your cryptographic inventory, ensuring agility and continuous progress.
06
Quantitative Quantum Risk is Essential to Building Your Quantum Resilience Roadmap.
QryptoCyber’s path to quantum resilience starts with a comprehensive cryptographic inventory—an essential step that can be completed in weeks. Yet, for large organizations, reaching a fully quantum-ready state may take years due to the extensive embedded legacy cryptography across systems and networks. Our structured roadmap includes:
Discovery
Mapping cryptographic systems across the five pillars—External Network, Internal Network, IT Assets, Databases, and Code.
Continuous CBOM
Maintaining an up-to-date Cryptography Bill of Materials to monitor all cryptographic assets and prevent exposures.
Time & Resources
Mapping cryptographic systems across the five pillars—External Network, Internal Network, IT Assets, Databases, and Code.
Why Quantitative Quantum Risk is Key
Quantitative Quantum Risk provides a high-resolution, financial view of quantum vulnerabilities. Leveraging principles of Cyber Risk Quantification, our solution offers:
Clear Exposure & Cost Metrics
Real-time, data-driven insights on quantum risks tailored to your cryptographic landscape.
Defensible Decision-Making
Empower leaders with concrete data for weighing the costs of upgrading legacy systems
Intuitive, Versatile Reporting
Deliver detailed reports for CISOs and executives, enhancing cross-department understanding and supporting strategic buy-in for quantum risk initiatives.