Quantum-Readiness: Migration to Post-Quantum Cryptography
Cryptographic Inventory
We fulfill CISA’s requirements for cryptographic discovery, inventory & risk assessment today.
Build an inventory of quantum-vulnerable technology and associated criticality of the data
Prioritization of Key Assets
Protect the most sensitive and critical datasets & correlate cryptographic inventory
Identify in processes
Identify quantum-vulnerable cryptography that protects critical processes
Identify in products
Identify embedded cryptography used internally within products
August 21, 2023
Quantum-Readiness: Migration to Post-Quantum Cryptography
This factsheet was created by CISA, NSA, and NIST to inform organizations, especially those that support critical infrastructure, about the impacts of quantum capabilities.
The Cybersecurity and Infrastructure Security Agency (CISA), the National Security Agency (NSA), and the National Institute of Standards and Technology (NIST) created this factsheet to inform organizations — especially those that support Critical Infrastructure.
This is what we do.
FROM THE FACTSHEET
Preparing A Cryptographic Inventory
Having an inventory of quantum-vulnerable technology and associated criticality of the data enables an organization to begin planning for risk assessment processes to prioritize its migration to PQC. Our cryptographic inventory will:
- Help an organization become quantum-ready — a state where a CRQC is not a threat,
- Help an organization prepare a transition to zero trust architecture,
- Help identify or correlate outside access to datasets, as those are more exposed and at higher risk, and Inform future analysis by identifying what data may be targeted now and decrypted when a CRQC is available.
Identify quantum-vulnerable algorithms
Identify embedded cryptography used internally within networks, end user systems, applications and products.
Find assets on end user systems and servers, including applications and associated libraries, both within application functionality and for firmware and software updates,
Correlate cryptographic inventory existing programs
Such as:
- Asset Inventory
- Identity, Credential, and Access Management, (ICAM)
- Identity & Access
Management (IdAM) - Endpoint Detection and Response (EDR)
- Continuous Diagnostics
and Mitigation (CDM)
Quantum-vulnerable cryptography
Identify quantum-vulnerable cryptography that protects critical processes, especially for Critical Infrastructure.
Why Prepare Now?
From the factsheet:
“A successful post-quantum cryptography migration will take time to plan and conduct. CISA, NSA, and NIST urge organizations to begin preparing now by creating quantum-readiness roadmaps, conducting inventories, applying risk assessments and analysis…”
You should start right now
QryptoCyber makes it easy and simple to execute on CISA’s requirements. This is our purpose. This is what we do. This is why we exist.
”So, from a private sector standpoint, I’d really be looking for some out of the box thinking and also understanding that it might be 10 years out but just assume that it’s 2 years out and that’s really the mindset that really needs to permeate throughout the different vendors, and I know that we’re going to be looking for in the FAA side especially.
Luci Holemans, CISSP, PMPCybersecurity Advisor, United States Space Force/FAA
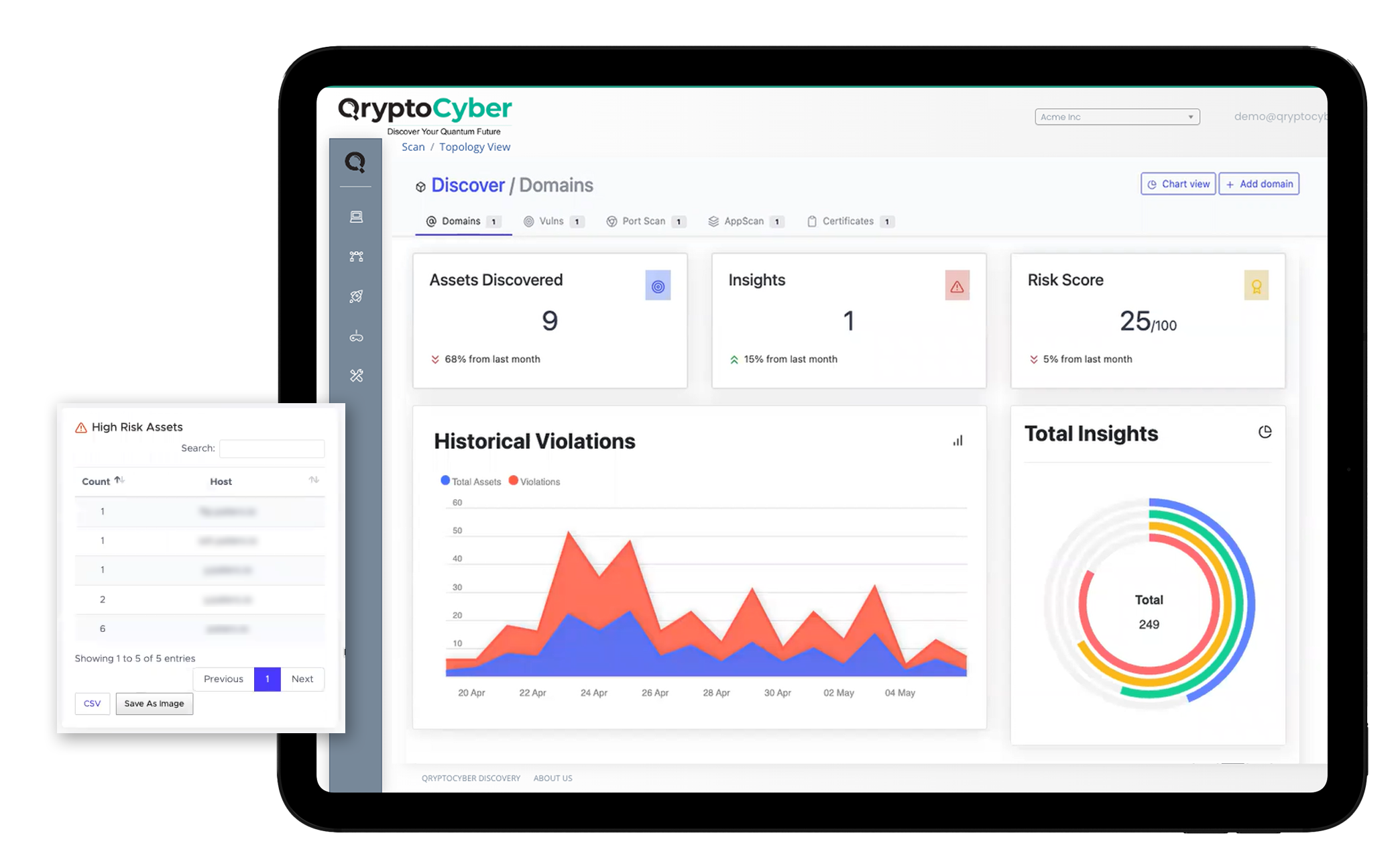
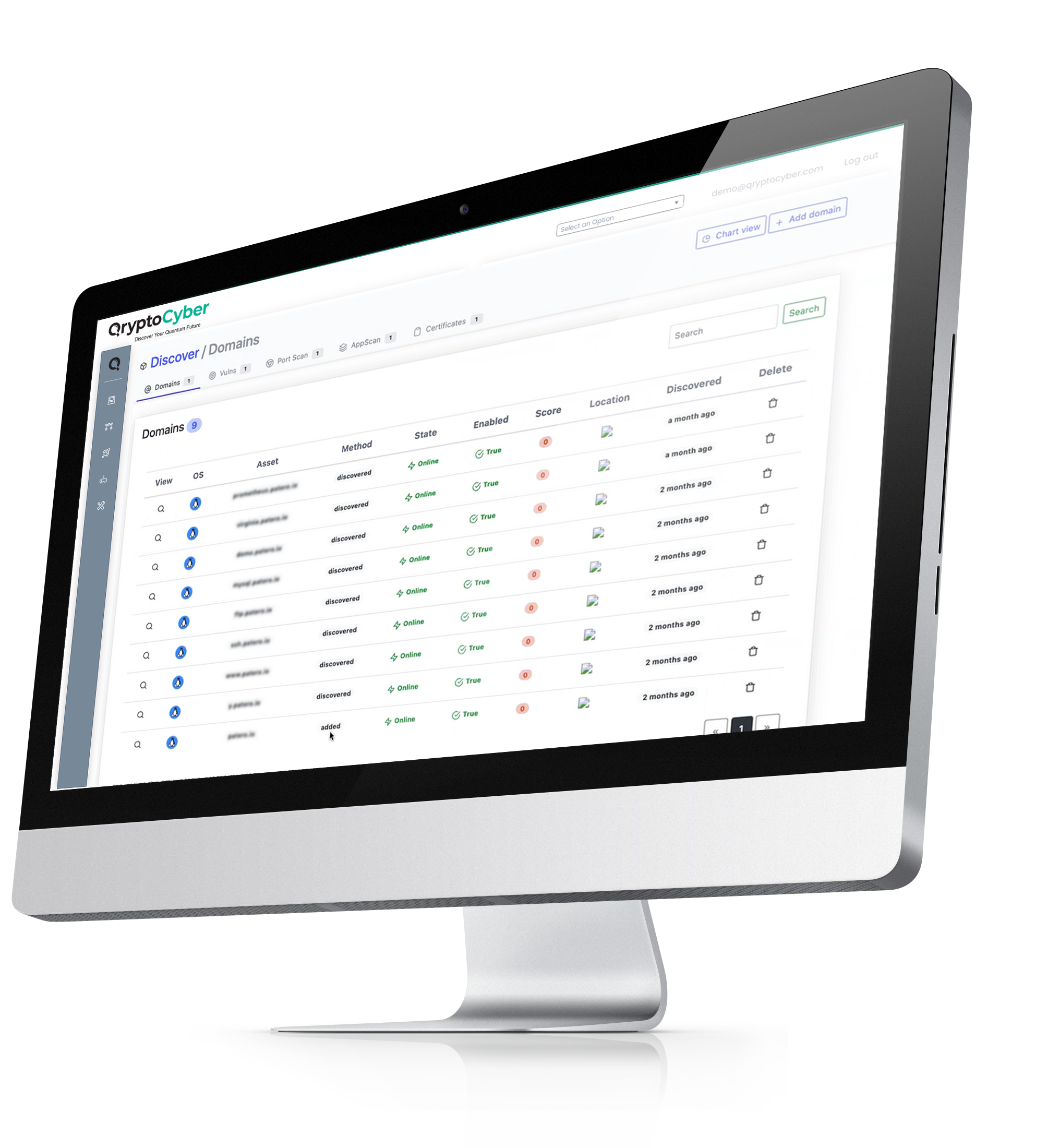
Our platform is based on different discovery types
This automated, intelligent encryption discovery is aggregated and scored using the QryptoCyber portal or API
External Network (Outside In)
- Our external encryption scanning service provides comprehensive visibility into the encryption methods, cipher suites, and protocols your organization is publicly exposing across the internet.
Internal Network (Inside Out)
- Our fully deployable internal encryption scanning solution allows you to discover and inventory encryption in use across your internal network.
These automated, intelligent encryption discovery services are aggregated, scored, and made actionable through the QryptoCyber portal or API, providing clear visibility across all five pillars of Cryptographic Discovery & Inventory.
Starting is the easiest part.
The problem won’t get easier with time. The first step is both the simplest and easiest. Put your foot on the path and start walking to the post quantum future.

