Find your internal
encryption.

Step 1 for Post-Quantum Cryptography Transition is Inventory: The Five Pillars of Cryptographic Discovery & Inventory.
In minutes. Continuously.
Internal Encryption Inventory. Fully in Your Control.
QryptoCyber’s internal encryption scanning capabilities are available as a fully deployable software package—giving you complete control over encryption discovery and inventory within your internal environment.
It’s API-driven, so you can integrate cryptographic findings directly into your existing tools or manage everything through the QryptoCyber platform.
Fast to deploy, easy to use, and built to support your quantum readiness from the inside out.
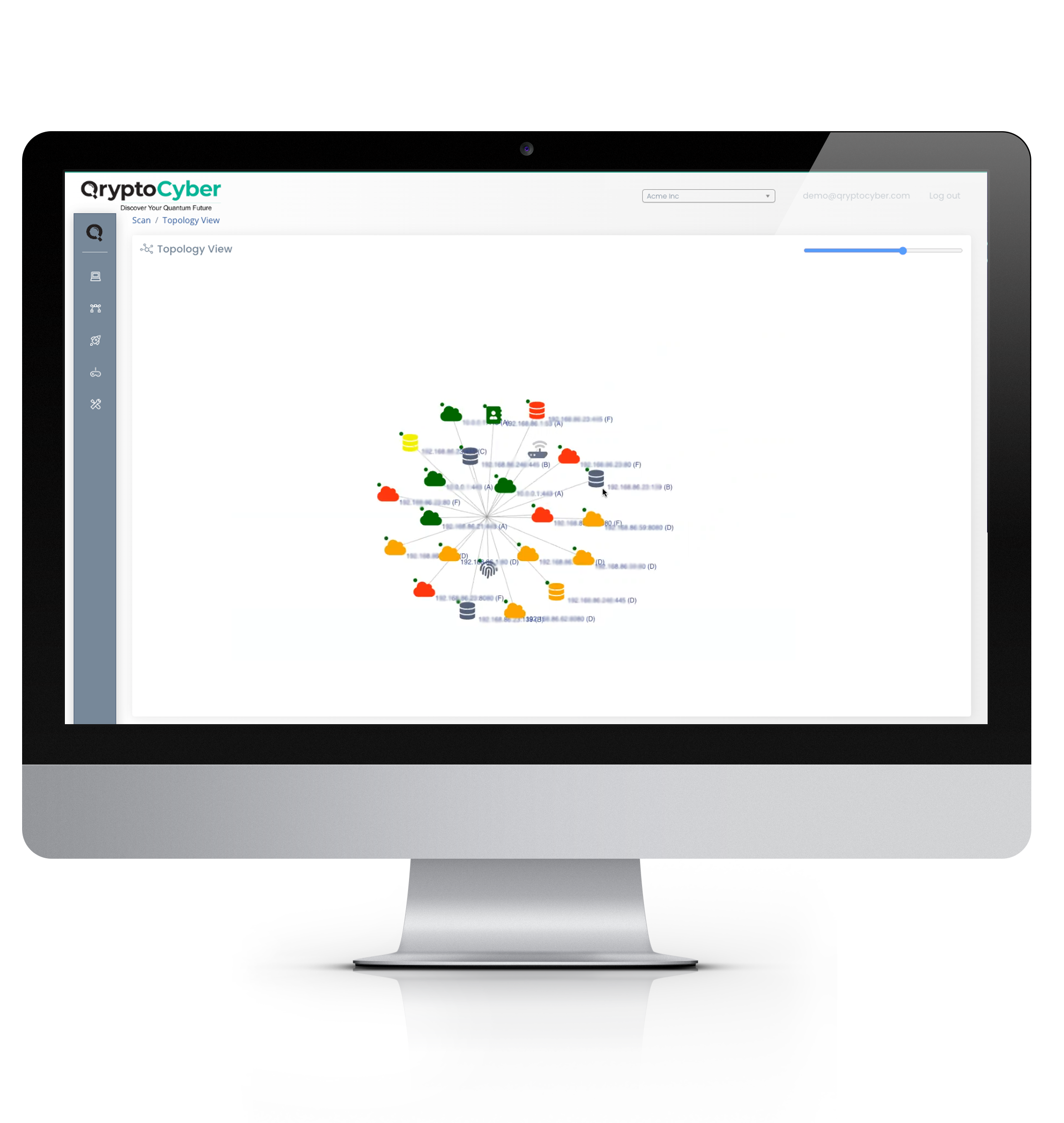
Internal Network Inventory
The second pillar addresses encryption within the Internal Network, focusing on how data is secured as it moves between internal systems, databases, and devices. A complete cryptographic inventory—plus a CBOM—lays the foundation for transitioning to quantum‑safe cryptography.
Data In Transit
Encryption plays a critical role in securing data in transit within the organization’s perimeter, especially in environments that handle sensitive information like healthcare, financial, and personal data.
Part of a Complete Inventory
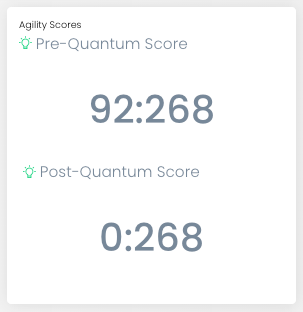
A complete cryptographic inventory not only enables you to identify your current encryption methods and assets but also lays the foundation for building a Cryptography Bill of Materials (CBOM)—a vital resource for transitioning to quantum-safe cryptography.
Encryption protocols used in internal communications must be reviewed to ensure their resilience to quantum threats
Identify encryption used for internal communications
This includes the encryption of internal APIs, cloud services, and internal messaging systems. Is data being transmitted securely between systems?
01
Verify the use of secure protocols
Outdated protocols like SSL and older versions of TLS should be flagged and replaced with quantum-resistant alternatives.
02
Monitor encryption configuration
Ensure that internal encryption is properly configured to minimize vulnerabilities. Misconfigurations can lead to unnecessary exposure of sensitive data, even within the internal network.
03
Flexible Deployment Options:
Your agent or ours?
See our specifications for details
QryptoCyber can now be configured to use a variety of commonly deployed agents for internal scans.
Encryption is everywhere in your network: applications, databases, hardware… well everything.
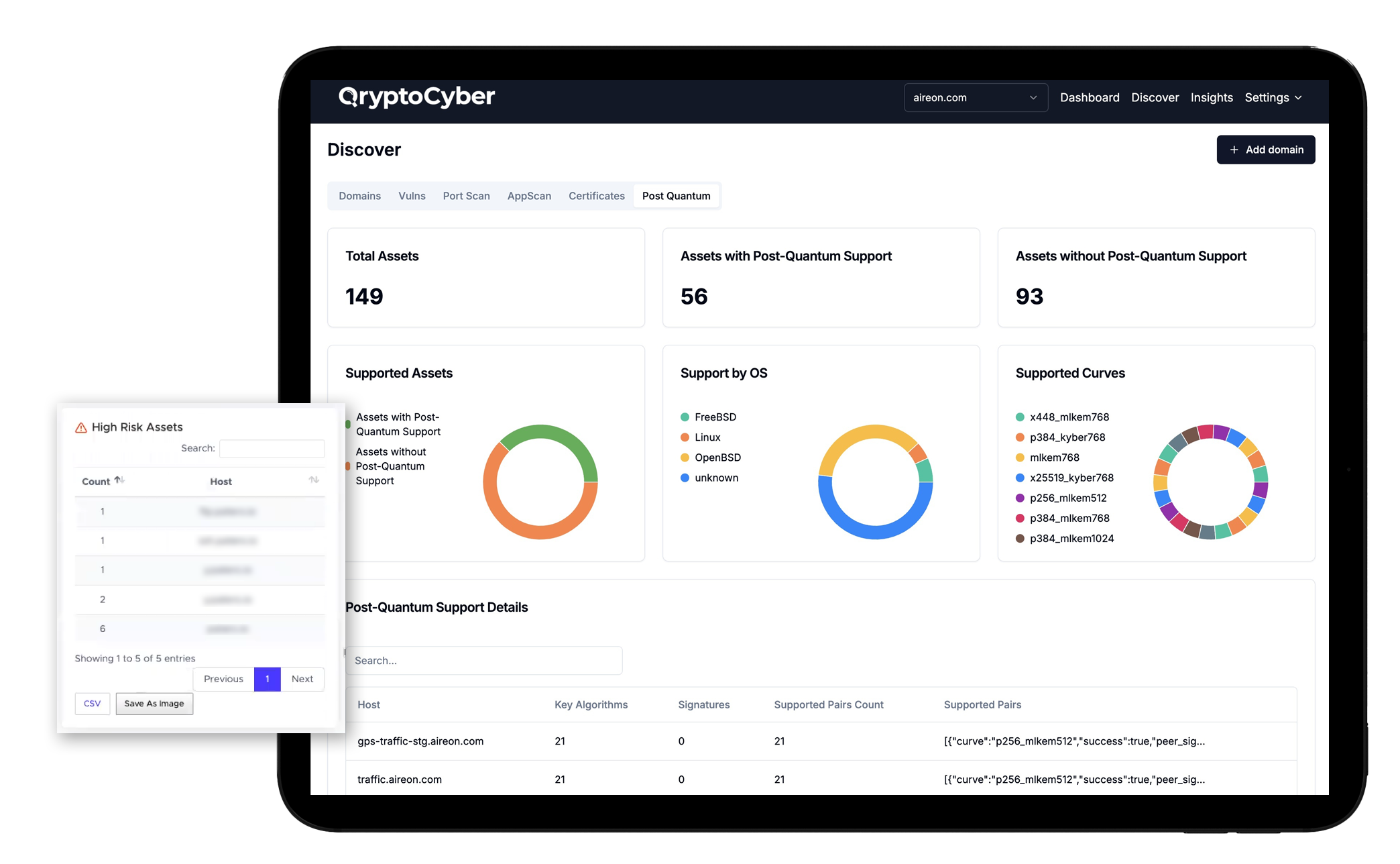
Discover and Identify Cryptographic Elements
Data moving across networks or between systems (e.g., through APIs, internal networks, or external communications) must also be identified and protected using secure encryption methods.
Network scanners monitor data moving through the network, looking for unencrypted traffic or deprecated cryptographic protocols.
Starting is the easiest part.
The problem won’t get easier with time. The first step is both the simplest and easiest. Put your foot on the path and start walking to the post quantum future.

