Zero to PQC

Nothing is holding you back.
Quantum and cryptography may be complex, but using Cryptographic AI² isn’t. We’ve trained the model to handle the hard parts so you don’t have to.
- All-In-One, All Done for You.
- No guesswork.
- No expertise required.
- No barriers to starting.
01
No Special Knowledge Required.
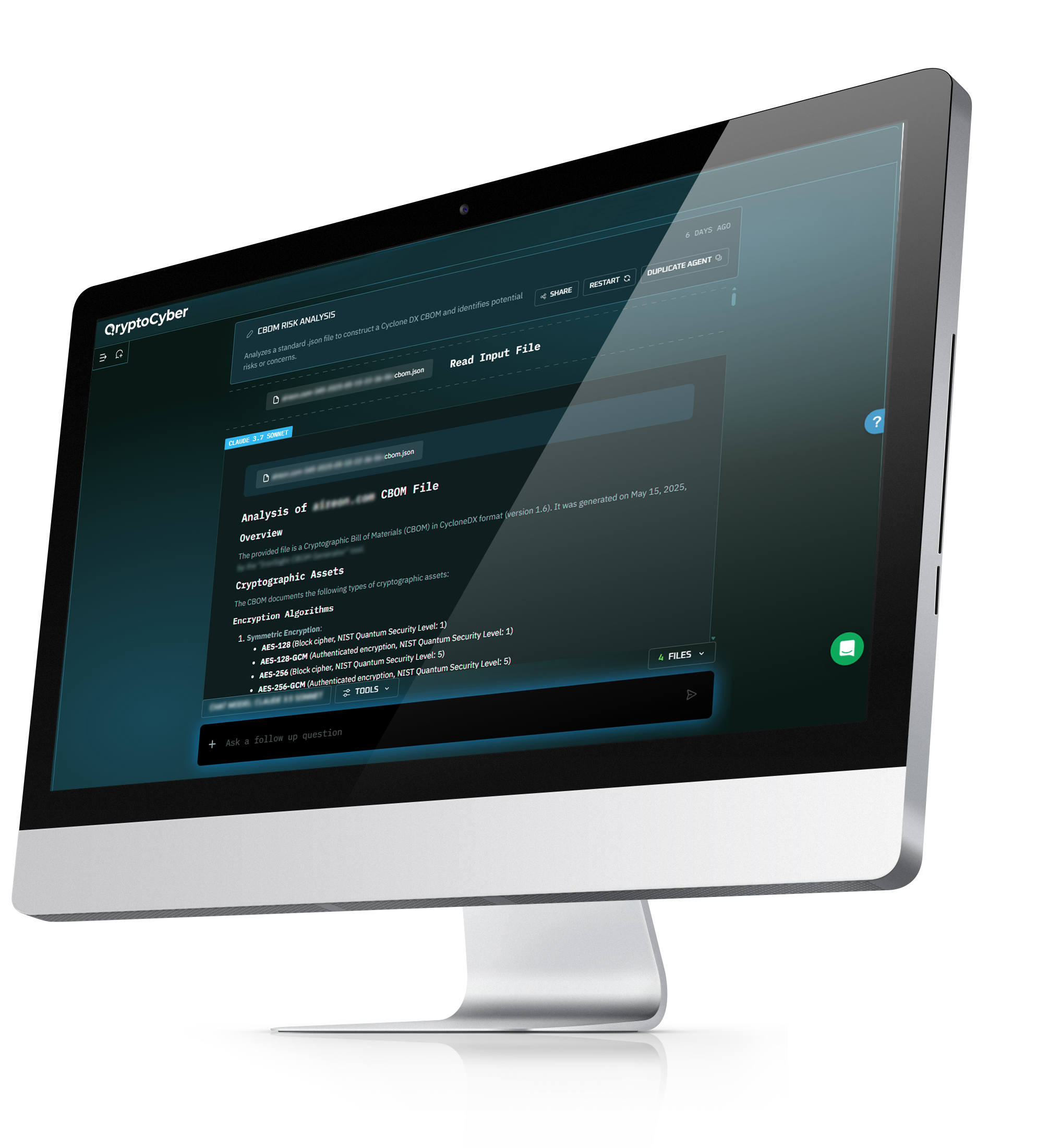
Cryptographic Adaptive Inventory Artificial Intelligence (Cryptographic AI²) takes your specific environment: tools, assets, and cryptography and builds your PQC strategy from the ground up.
02
Not Complicated. AI That Adapts to You.
We take care of all the complicated bits. The AI adapts to your tech stack and organizational structure. It transforms a static cryptographic inventory into a fully actionable plan.
03
Too Easy? You have other things to do.
Automatically integrates with your existing tools, reporting systems, and data flows via our built-in orchestration layer.
04
PQC Services: Hand the whole project over.
Our partners (or yours) can handle the full remediation effort, with cleared, on-site, or outsourced staffing options as needed.
The difference
Transforming static Cryptographic Bills of Materials (CBOMs) into dynamic, continuously adaptive cryptographic management systems.
CBOM Limitations
Historically, CBOMs quickly became outdated static snapshots, failing to address evolving threats and leaving organizations exposed.
Proactive, actionable security management
Recognizing these critical limitations, and adding AI into the mix, QryptoCyber developed Cryptographic AI² to bridge the gap between cryptographic inventory data and proactive, actionable security management.
Designed by Security Professionals, for Security Professionals
No AI Agents in Your Network
The AI Sandwich: AI ➝ Inventory ➝ AI
Cryptographic AI² powers a closed-loop system that plans, gathers, and adapts—continuously improving your quantum readiness program without adding risk or overhead.
All of this happens without deploying AI agents in your network. It's cryptographic transformation done the right way: secure, scalable, and built for real-world security teams.
AI Planning
Cryptographic AI² generates the plan and builds your quantum program based on your individual tech stack and cryptographic posture.
Inventory via your tech stack
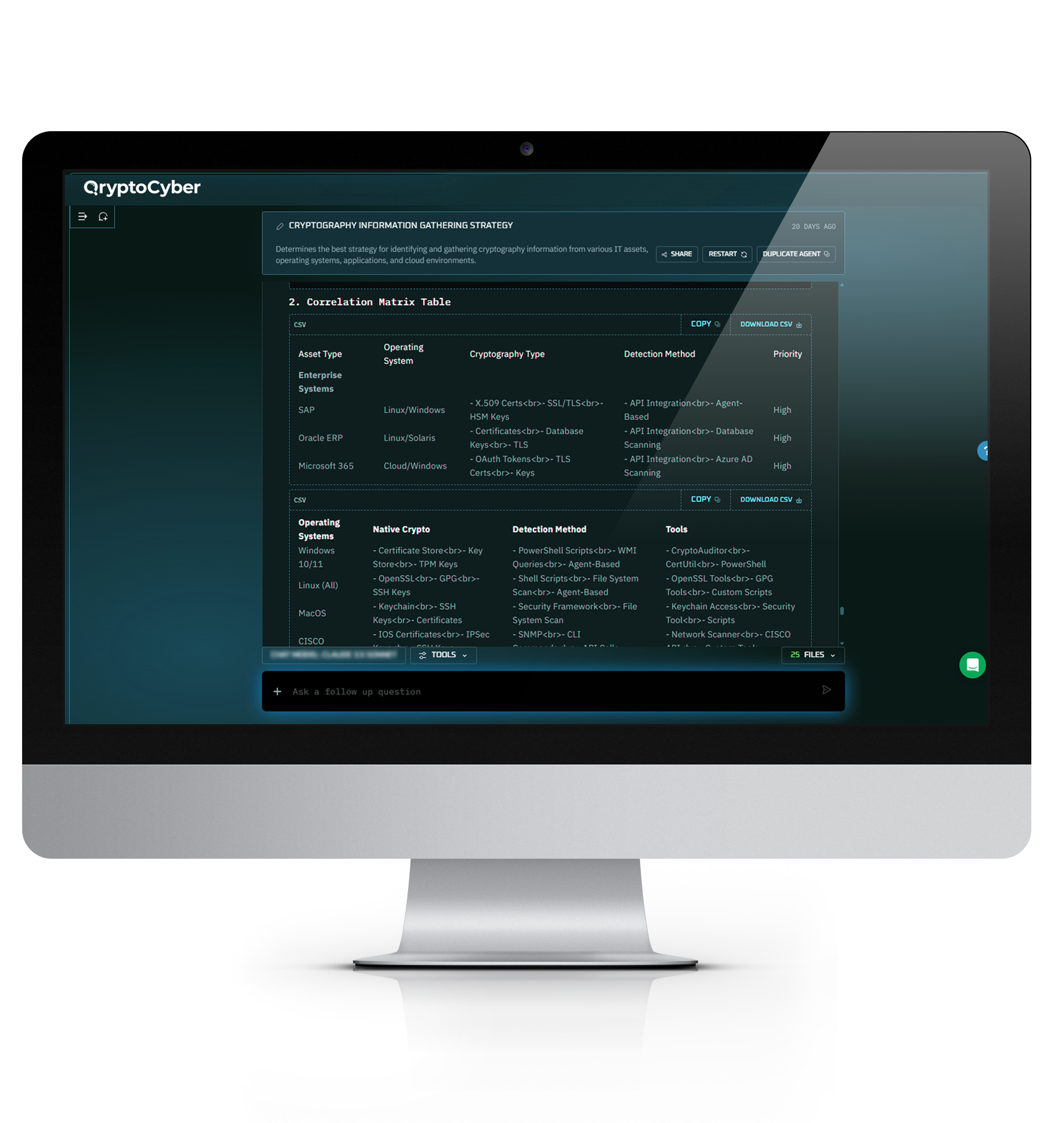
Your five-pillar inventory: External Network, Internal Network, IT Assets, Databases, and Code, is gathered using your existing tools and agents. No new endpoint or network agents are required.
AI PQC Roadmap
The Cryptographic AI² model continuously updates your roadmap based on real-time inventory changes… keeping your CBOM current and your post-quantum transition aligned with actual risks and priorities.
Cryptographic AI² delivers comprehensive, real-time cryptographic management capabilities:
Starting is the easiest part.
The problem won’t get easier with time. The first step is both the simplest and easiest. Put your foot on the path and start walking to the post quantum future. [Start here]

