START HERE. THIS IS THE LONG EXPLANATION.
SHORTER VERSION IS UNDER SOLUTIONS.
The state of encryption today is precarious. Cryptographic systems, no matter how robust they seem, have a finite lifespan. They will eventually be broken, whether by quantum computing, advanced algorithms, specialized circuits, or a combination thereof. The question is not if, but when.
Heads-Up: Crypto’s About to Get a Whole Lot More Complicated
RSA and public key encryption? Yeah, they’re on borrowed time. Quantum computers, specialized circuits, AI, or some new algorithmic wizardry—one way or another, they’re going down. When exactly? Doesn’t matter.
What matters is that new encryption standards are just months away. And you’ll need to get on board. This will help you understand where the industry stands right now and give you a peek into the future.
FUD Up Front
Quantum threats have a lot of fear, uncertainty, and doubt surrounding the entire subject. So, we’re going to address some of these right now.
The quantum revolution will disrupt many industries for the betterment of society, but one aspect of quantum computers will bring about a long-overdue change in cybersecurity. Quantum computers with appropriate algorithms will be able to break many current encryption standards. This could be combined with AI, specialized circuits or alien black magic tech to make it work.
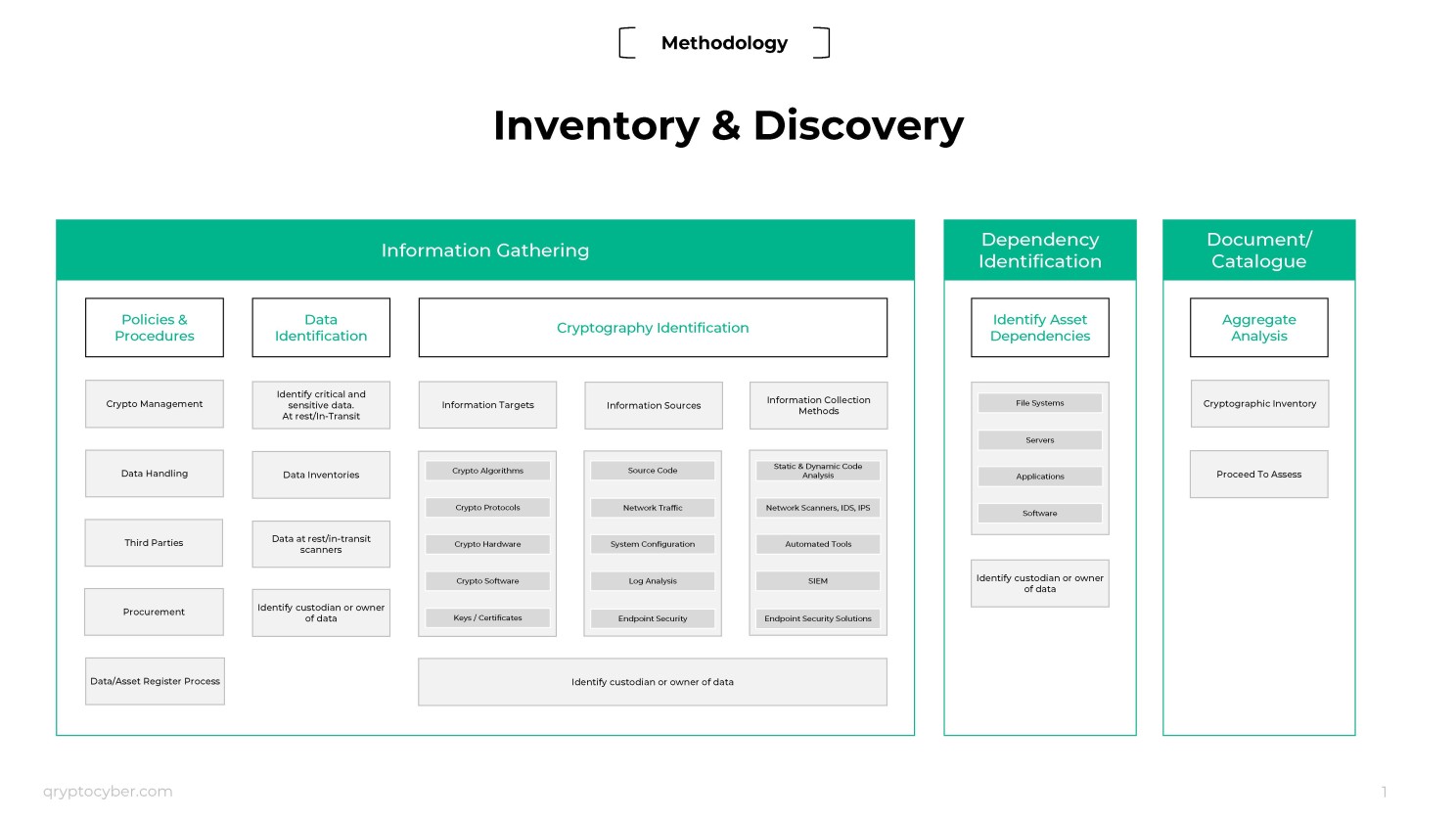
The majority of organizations do not currently track what encryption standards are in use. This is a problem.
Although they met a minimum standard when implemented, they did not keep track of where and what they are. To change these cryptographic systems, they must first find and inventory them.
This is a fundamental shift in thinking for security organizations. Previously, they had used vendors and commercially available systems. Now, security organizations must track and manage cryptography themselves for the foreseeable future.
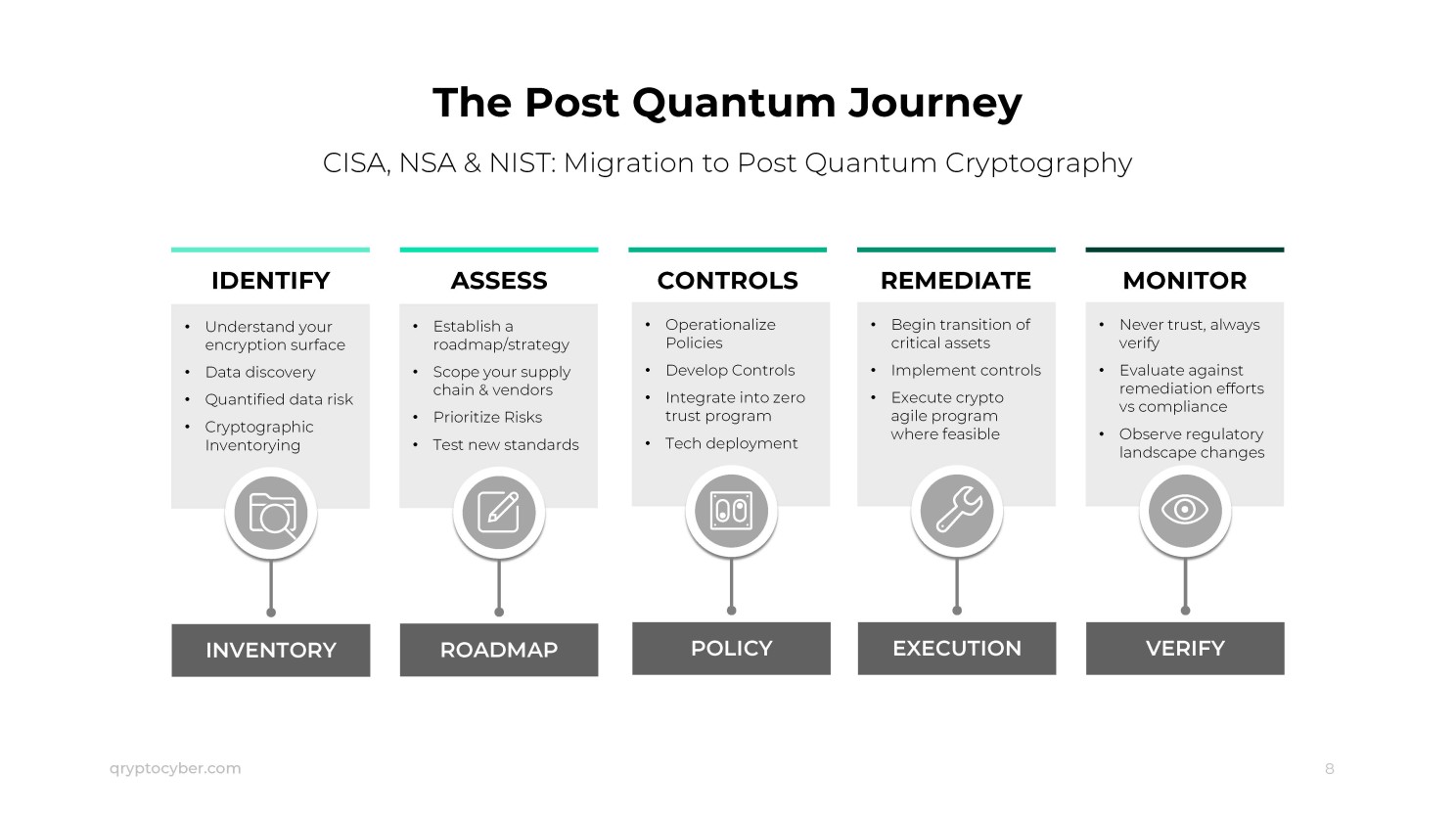
Discovery, inventory, and analysis are the first steps to becoming quantum-safe, and all organizations need to accomplish this in the next few years.
We should be already doing this.
Spoiler alert: none of these matter as regulations are changing and you’re going to have to comply anyway. PCI DSS 4 already requires it.
Terms to know
But let’s address some of the reasons why you’re reading this. Note: much of this is explained in depth, but I wanted to let the boomers get comfy.
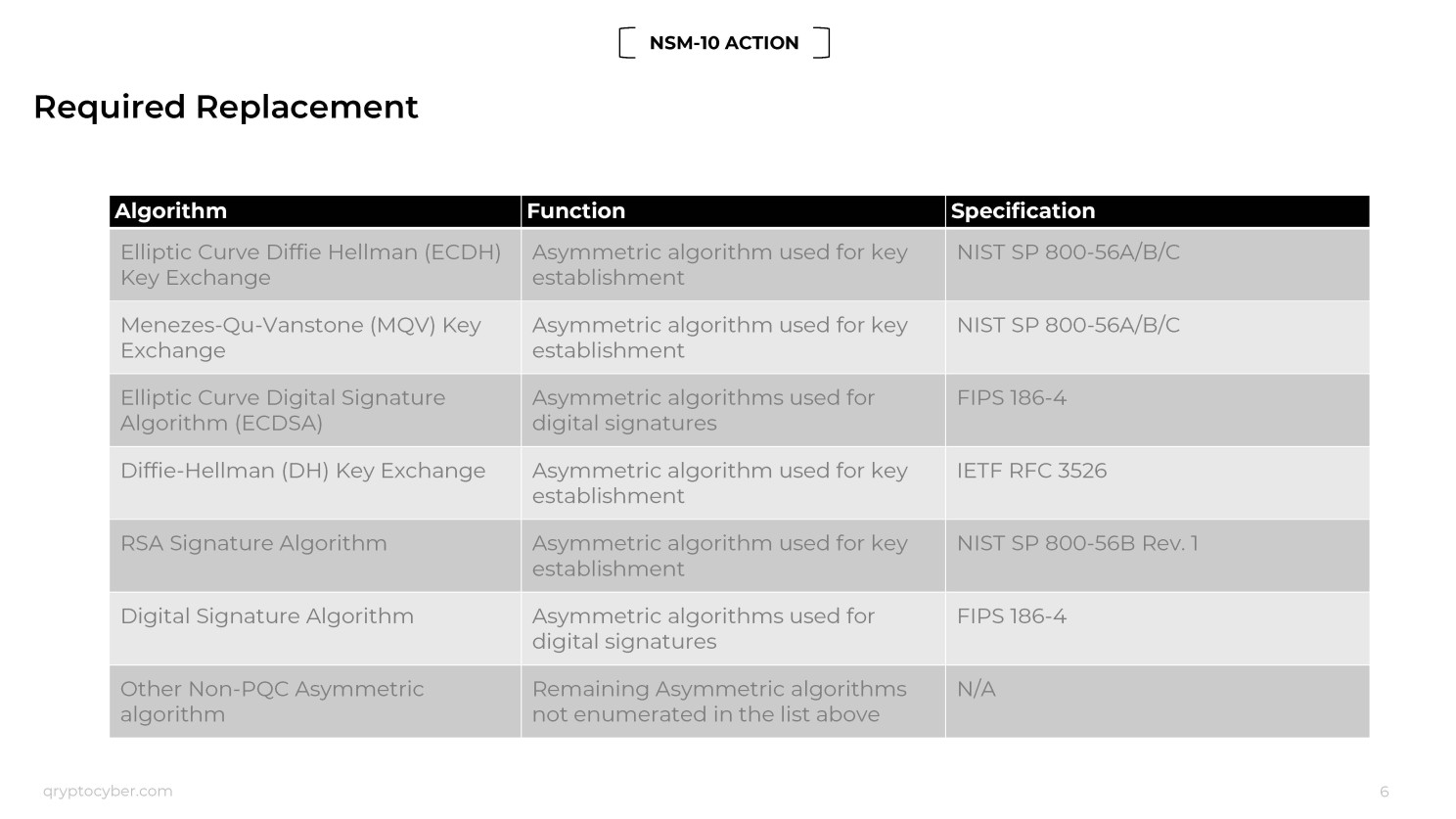
NSM-10: The U.S. Government believes that public key encryption is broken or will be broken in the very near future, mostly due to quantum computers but potentially also due to machine learning, AI, and special hardware.
Harvest Now, Decrypt Later (HNDL) Attacks: This is the FUD (fear, uncertainty, and doubt) part. Storage is cheap, so why wouldn’t nation-states devote some effort to this? While unencrypted data is hard to sort and prioritize, unless you have specific data that a nation-state could operationalize, this isn’t a major worry for you. These attacks are sometimes called Store Now, Decrypt Later (SNDL) attacks. We prefer HNDL because we’ll handle it.
Shor’s Algorithm: Devised by mathematician Peter Shor in 1994, this quantum algorithm efficiently factorizes large composite numbers into their prime factors, which is significant for breaking widely used public-key cryptosystems like RSA. Shor’s algorithm requires a massive amount of quantum computing power with great error correction (very grossly simplified). We are nowhere close to using Shor as it was conceived in 1994.
Q-Day: This is the day when quantum computers can break public key encryption. The U.S. Government thinks it is soon, but academia estimates it is 15-25 years away. If we use Shor as a guide, academia is probably correct, but keep in mind that algorithms can be state secrets, and mathematics hasn’t stood still for the last 30 years. Some U.S. Government folks are pushing two years as the breaking point. They could be wrong, but if those spooks know something, they aren’t sharing. It doesn’t matter anyway, as NIST will put out the timeline, and that’s what everyone will follow.
Post Quantum Cryptography (PQC): We don’t yet know the long-term viability of new PQC systems. Expect some to be broken much sooner than RSA’s lifespan. Developing a crypto agility program is wise. NIST-approved algorithms will be available soon, and there are commercially available ones and a NIST pipeline as well.
Symmetric-Key Encryption: Symmetric-key encryption is expected to withstand quantum attacks. The security relies on the strength of the key and the encryption algorithm. Advanced Encryption Standard (AES) should be robust enough, but key distribution remains a challenge.
Crypto Agility: This means that any data can be encrypted with any cryptographic protocol at any time, either on a pre-set schedule, with a variety of protocols, or in response to external stimuli. Flexibility is essential as we enter an uncertain time for cryptography (and we should be doing this anyway). More details below.
What, Me Worry?: If you’re old enough to get that reference, you know how much can change over a lifetime. For the younger generation, don’t be shocked that things change, and get used to it. Seriously though, if your role is to protect data from nation-states, you need to worry and get moving. If you protect transactional data, you can take your time.
Why You Should Care
(Right Now)
PKI is dead. We just haven’t accepted it yet.
Public Key Infrastructure (PKI) is a set of hardware, software, policies, and standards that work together to provide a framework for secure communication and digital signatures. PKI uses asymmetric cryptography, which involves the use of public and private key pairs.
PKI is widely used to establish a secure communication channel over the internet, ensuring the confidentiality and integrity of data. It is commonly employed in applications such as secure email communication, digital signatures, SSL/TLS for secure web browsing, and Virtual Private Networks (VPNs).
What’s at stake: do you care if a nation state gets your data?
Moody’s, a ratings agency, has issued a warning that companies are inadequately prepared for the risks and impacts of quantum computing. This includes the need to update systems for post-quantum cybersecurity. According to one analyst, large organizations should have already taken steps to brace themselves for the technology’s impending impact.
In a recent quantum research report, Moody’s consulted with 200 leaders in data, analytics, and innovation within financial services and banking companies across Europe and North America. The report revealed that 87% of these companies lack the necessary budget to make substantial investments in quantum technology.
Despite government and cybersecurity warnings about the potential threat of quantum computers breaking encryption, the report found that 86% of surveyed companies are not ready for post-quantum cybersecurity. This is particularly concerning given that 84% of them acknowledge the need to be prepared within the next 2-5 years.
Nation-states are always looking for opportunities to outcompete or gain an advantage over other states. Likewise, some commercial entities are on the lookout for opportunities to do the same. Some entities combine both commercial and state functions for the benefit of the state, individuals, or both. Most organizations would like to keep their secrets and not broadcast them publicly and in the clear. Data sovereignty for governments and data protection for commercial companies are vital to their interests.
The financial services sector is recognized as an early adopter of quantum technology, as even current quantum hardware can make an impact on functions like fraud detection and solving optimization problems. Most companies exploring quantum computing believe that risk analysis holds the greatest potential for influencing the financial services sector, given its compatibility with the way quantum hardware processes a significant number of variables and points of consideration.
Transactional data probably has little value to those states with the capabilities to bring this technology to bear on you. If you have data that adversarial nations would love to have, then you need to pay attention and get things moving now.
Protect against nation state actors
Everyone should be worried. But to be clear, it is most likely that these will be nation state actors who will be able to leverage cryptographically relevant quantum computers (CRQC) or other combinations of specialized circuits, machine learning/AI, new mathematics or and specialized quantum computing.
The sky is falling but only for those that have data valuable to nation states. Thus, a national chain of restaurants wouldn’t be of concern but… financials must be concerned today. A single-day quantum computer attack on a top-five bank would cost the US economy between $2 and $3.3 trillion in indirect impacts alone.
As quantum advancements draw near, organizations find themselves at varying levels of readiness. Historical shifts in cryptographic standards and algorithms have occurred, with certain industries still grappling to transition to standards from a decade ago. Given the transformative nature of quantum computing, organizations cannot afford to lag behind. We are committed to furnishing you with the necessary resources to establish the foundations for a quantum-ready future.
Are you the priority target of nefarious state-based actors looking to harvest sensitive information now, with the intention of decrypting it later? Harvest Now, Decrypt Later (HNDL) attacks are a real threat. There is no hard intel that is openly shared on who is doing this. This is fear, uncertainty, and doubt (FUD), but strictly logical FUD. It is probably happening because government intelligence agencies are hoarders and storage is cheap.
Secure supply chains
The growing worry about quantum attacks on supply chains stems from the potential of quantum computers to compromise widely employed cryptographic algorithms like RSA and ECC (Elliptic Curve Cryptography).
To address these risks, organizations must embrace quantum-resistant cryptographic techniques and incorporate additional security measures. As quantum technologies progress, proactive adaptation of security measures becomes crucial for organizations to stay ahead of potential threats. Regularly reassessing and updating security protocols will play a crucial role in preserving the resilience of supply chain systems.
Create a Crypto-Agile Legacy
Whether you hold the role of a Chief Information Security Officer (CISO), a developer, or fall anywhere in between, allocating time for this challenge is imperative.
Whether prepared or not, a forthcoming era in security is imminent. This spans the art of strategic planning to the intricacies of testing and implementing new algorithms. Becoming quantum-ready is complex and requires collaboration with various hardware, software, and service providers.
Crypto Hardware
Cryptographic hardware refers to specialized hardware components and devices designed to perform cryptographic operations securely and efficiently. These components are dedicated to handling cryptographic algorithms and functions, providing a higher level of security compared to software-based solutions. Cryptographic hardware is commonly used to secure sensitive information, protect communication channels, and authenticate users. Using cryptographic hardware can enhance the security of systems and applications. It provides dedicated and isolated environments for cryptographic operations, protecting sensitive information from various types of attacks.
Securing the keys
Hardware Security Modules (HSMs) are dedicated devices that provide secure key management and cryptographic operations. They are commonly utilized to generate, store, and manage cryptographic keys, as well as to perform encryption and decryption operations. HSMs are tamper-resistant and designed to protect cryptographic keys from unauthorized access.
The New Math: Risk Bingo
Breaking RSA
In-memory computing ASICs offer a non-quantum approach to large-scale prime factorization directly on a chip. Enter MemComputing’s combined memory/processing approach. Simulations demonstrate that the complexity/time ratio for solving challenging problems increases only polynomially, rather than exponentially. In other words, difficult problems can be solved much faster — with significantly reduced time requirements. Who needs quantum computing when you have memory-crunching computers?
AI/ML
Quantum cryptography and AI are two distinct but potentially complementary fields. Quantum cryptography utilizes the principles of quantum mechanics to secure communication channels, while AI involves developing intelligent systems capable of learning and decision-making. Quantum computing, a related field, may impact AI through quantum machine learning algorithms. Quantum computers have the potential to solve certain types of problems much faster than classical computers. By applying quantum machine learning algorithms, AI models could enhance their capabilities, processing complex information more efficiently.
”“Becoming quantum ready is like solving a jigsaw puzzle, except you don’t hold all pieces of it.”
- KPMG
New Algorithms, new techniques, oh my.
Now we’re diving into the tin foil hat portion of the show. Our full-on conspiracy theory suggests there might be new mathematics developed by adversaries to enhance Shor’s algorithm or even concoct some Frankensteinian amalgamation involving AI, classical computing, memcomputers, circuits, and qubits. This is nation-state-level stuff, so it’s both secretive and well-funded, likely in some country, somewhere.
The point is, where there’s a will, there’s a way. This is nothing new in the crypto world. We should maintain crypto agility, but that won’t be an easy task.
Winning the Lottery: Optimal End State is Crypto Agility: Any data, Any protocol, Any time
Crypto Agility isn’t just a strategy; it’s an ideal to strive for. It’s not about a specific framework or protocol but rather the flexibility to encrypt data with any cryptographic protocol at any time. This can be done on a pre-set schedule, using a variety of protocols, or in response to external stimuli.
In the future, multiple protocols will coexist simultaneously, providing an effect similar to sharding. This dynamic use of protocols makes decryption exceedingly difficult for attackers, even with a quantum computer. The principle is simple: never trust, always verify.
In cybersecurity and cryptography, crypto agility refers to the adaptability of cryptographic systems or algorithms in response to emerging threats or technological advances. It ensures that systems can transition smoothly to new cryptographic methods or key lengths without causing disruptions. This adaptability is crucial as older cryptographic methods may become vulnerable to attacks as computing power increases.
It’s important to note that the term ‘crypto agility’ may have different interpretations depending on the context, so it’s essential to consider the specific domain or application where the term is used.
”“Drafts of PQC standards have recently been released and with that, in 2024, I expect that we will see a new group of organizations begin to take steps towards quantum readiness – starting with assessments of their cryptographic exposure – while those who have already commenced that journey will add further to their cryptographic agility plans.”
Colin SoutarDeloitte’s managing director of risk and financial advisory
Living the Dream
Crypto agility is a strategy, not a framework or a product. It should be structured as both a proactive and reactive plan. A proactive strategy involves implementing policies, procedures, and technology to change algorithms on a predetermined schedule or employ multiple changing algorithms. Reactive crypto-agile playbooks are developed in case one or more algorithms in the inventory become deprecated, allowing for immediate utilization.
These strategies can be executed via orchestration or other automated technologies, minimizing the need for human intervention to implement a policy or course of action (i.e., simply “push the button”).
A Dream Doesn’t Become Reality Through Magic
The reality is that none of this actually exists beyond some algorithms. The entirety of how we use crypto systems is fundamentally flawed and must be rebuilt from scratch while in flight. We currently have a fixed state of encryption that needs to transition to a fluid state, with a large ‘miracle happens here’ moment in between.
We’re dealing with fixed hardware, legacy applications, and unknowable databases, all of which have encryption baked in with no easy way to fix them. There will need to be a plethora of band-aid technologies created for these items, either because they can’t be replaced or because replacement would be prohibitively expensive before the end of their life.
Each and every aspect will need to be either updated (preferable), removed (less so), or isolated and wrapped inside a new crypto system. But not all at once. As always, knowing where your most important data resides is highly desirable.
Embarking on the journey to become quantum-ready is like solving a puzzle without all the pieces. Achieving a quantum-ready state requires a clear internal understanding of the cryptographic landscape and a thorough comprehension of the associated risks. Mitigating these risks involves collaborative efforts with specialized service providers and relying on external organizations to enhance cryptographic and security protocols and controls.
About Us:
QryptoCyber makes it possible to know what encryption you have, where it is and how much risk it poses to the organization.
The largest companies, organizations, and governments are already moving towards the quantum age with this agility in mind, but everyone else must prioritize their quantum calculus in order to maintain near-peer competition.
Having an inventory of quantum-vulnerable technology and associated criticality of the data enables an organization to begin planning for risk assessment processes to prioritize its migration to PQC. Our cryptographic inventory will:
- Help an organization become quantum-ready — a state where a CRQC is not a threat,
- Help an organization prepare a transition to zero trust architecture,
- Help identify or correlate outside access to datasets, as those are more exposed and at higher risk, and Inform future analysis by identifying what data may be targeted now and decrypted when a CRQC is available.
https://qryptocyber.com/quantum-readiness-cryptographic-inventory/
QryptoCyber makes it easy and simple to execute on CISA’s requirements. This is our purpose. This is what we do. This is why we exist.
Thanks for reading.

