Step 1 for Post-Quantum Cryptography Transition is Inventory: The Five Pillars of Cryptographic Discovery & Inventory.
Asset Encryption Scanning


Asset Encryption Scanning
This pillar focuses on identifying encryption across your entire fleet of IT and IoT assets—laptops, servers, mobile devices, embedded systems, and more. These assets often store or process sensitive data, yet the encryption protecting them is frequently undocumented or misunderstood.
QryptoCyber scans these systems to discover how and where encryption is used—capturing ciphers, key lengths, certificates, protocols, and cryptographic libraries.
The result is a machine-readable Cryptographic Bill of Materials (CBOM) that becomes the foundation for risk analysis, remediation planning, and quantum-safe upgrades.
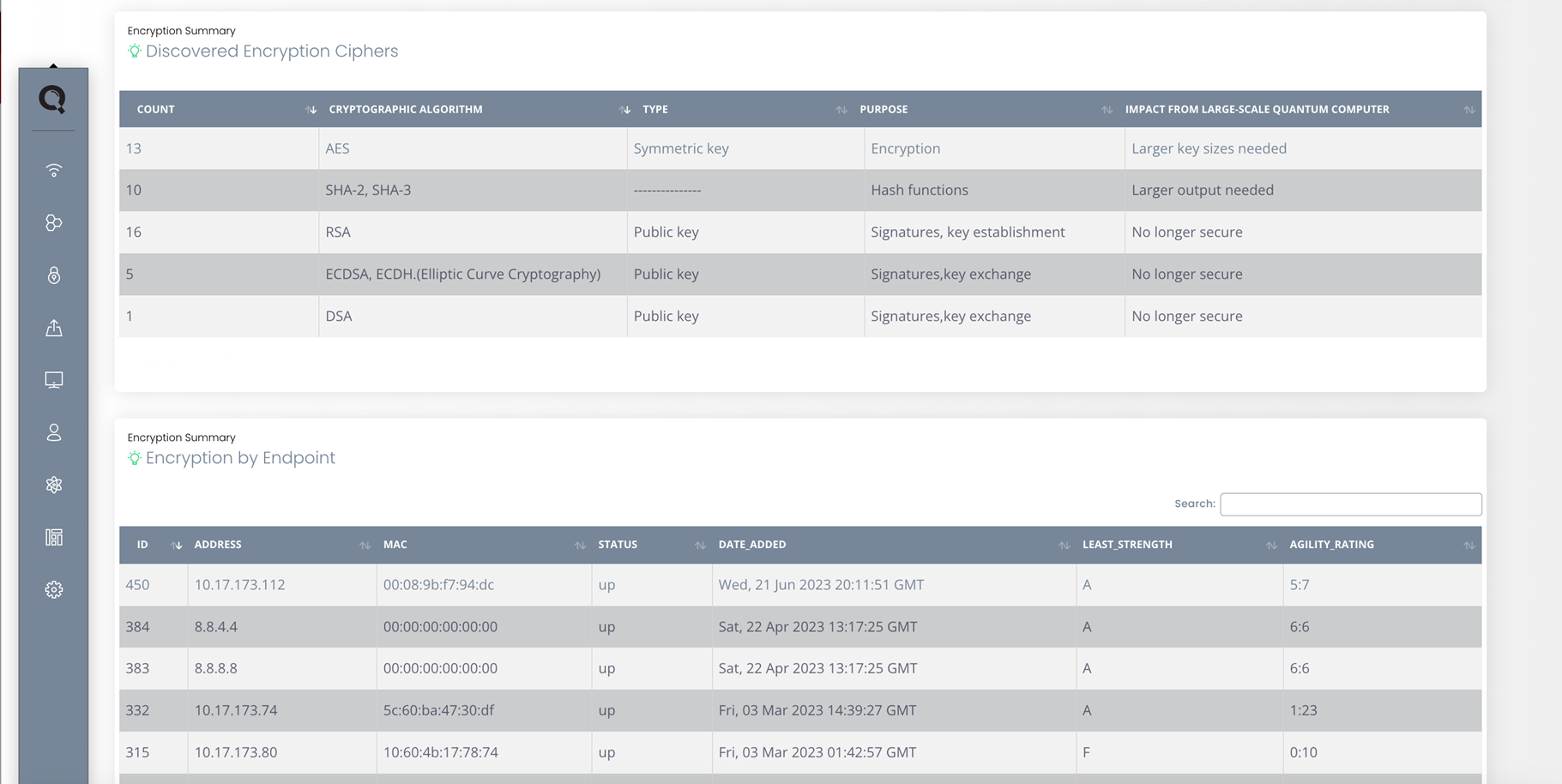
Ensure that encryption is applied to protect sensitive data stored on devices, such as employee laptops or mobile devices.
Outdated protocols like SSL and older versions of TLS should be flagged and replaced with quantum-resistant alternatives.
Critical data stored on servers should be encrypted both at rest and in transit. Outdated algorithms such as AES-128 should be upgraded to stronger quantum-safe standards, such as AES-256.
External (either Software As A Service, Private Cloud, Customer Provided environment), internally hosted as a docker image or consultant managed.
The problem won’t get easier with time. The first step is both the simplest and easiest. Put your foot on the path and start walking to the post quantum future.