Discover what Code is using
encryption.


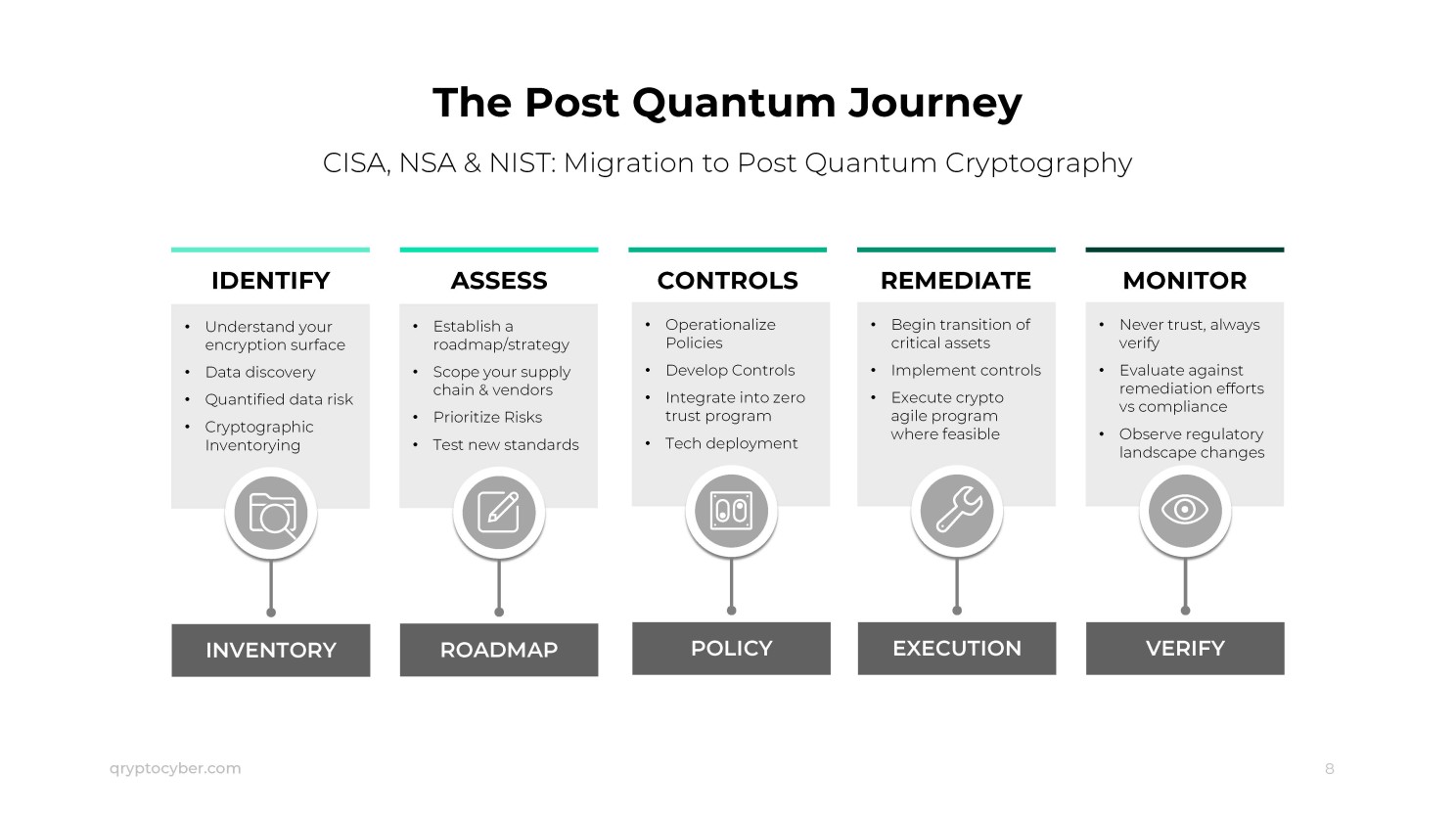
Step 1 for Post-Quantum Cryptography Transition is Inventory: The Five Pillars of Cryptographic Discovery & Inventory.
Encryption Code Scanning
Find, Analyze, and Inventory Code-Based Encryption
Effective encryption isn’t just about transport or storage—it’s embedded deep in your applications. Our scanning finds deprecated algorithms, hard‑coded keys, and vulnerable libraries, then catalogs everything into a CBOM for structural visibility and remediation planning
For encryption to be fully effective, organizations must know precisely where and how it’s being used across their codebases.
At QryptoCyber, we recognize the importance of gaining visibility into code-based encryption as part of a comprehensive Cryptographic Discovery & Inventory. This recognition forms the foundation of our fifth pillar: discovering encryption in code.
This final pillar, Code, can often be the most challenging to address because it requires deep analysis of potentially vast codebases to locate cryptographic methods, keys, and libraries.
However, this is also one of the most crucial areas for understanding encryption usage, as encryption embedded in code often forms the heart of an organization’s data security strategy.
Preparing for Quantum Resilience with Code-Level Encryption Visibility
Preparing for quantum-safe security means knowing what’s in your code. By generating a CBOM of your encryption assets, you can proactively replace outdated ciphers and secure your software against future threats.
Having a clear view of encryption within code is essential for organizations preparing for a quantum-resilient future. Quantum computing advancements are expected to disrupt traditional encryption methods, potentially rendering some obsolete. By identifying and cataloging encryption usage across codebases, organizations are empowered to proactively replace or update vulnerable cryptographic algorithms, setting a foundation for quantum security.
Code
The final pillar focuses on Code, emphasizing the need to search for and inventory encryption used within software applications and code libraries.
Encryption is often embedded deep within application logic, making it critical to identify vulnerable or deprecated algorithms used in proprietary or third-party code.
Organizations should:
Conduct a code review for cryptography
Search through code repositories to identify where cryptographic algorithms are implemented, whether through native code or third-party libraries.
01
Replace deprecated cryptographic algorithm
Ensure that legacy algorithms, such as MD5 or SHA-1, are replaced with modern, quantum-resistant alternatives.
02
Maintain an up-to-date cryptographic inventory
Create and maintain an inventory of all cryptographic algorithms used in the codebase, ensuring that developers follow best practices for post-quantum encryption.
03
Advanced Code Search and Analysis
Deep code analysis uncovers not just libraries but embedded secrets too. Our scan automates building a CBOM that logs every cryptographic asset and its context—ideal for securing CI/CD pipelines and tracing risk.
Locating encryption in code requires specialized search and analysis capabilities that can sift through complex repositories and identify cryptographic libraries, algorithms, and hardcoded keys.
QryptoCyber’s approach enables organizations to conduct detailed scans and find encryption implementations, whether they’re buried deep within modules or spread across multiple projects.
Discovering encryption within code isn’t just about finding libraries; it’s also about identifying sensitive information, like private keys or tokens, that shouldn’t be present in code repositories. With secret scanning capabilities, QryptoCyber helps clients pinpoint any sensitive cryptographic materials and securely manage them as part of their cryptographic inventory, reducing the risk of exposure.
QryptoCyber’s Commitment to Comprehensive Cryptographic Discovery & Inventory
At QryptoCyber, our Cryptographic Discovery & Inventory model is designed to help clients achieve full encryption visibility, including the often-overlooked area of code.
With our robust approach to finding encryption within code, clients gain the confidence of knowing their cryptographic materials are secure, controlled, and ready for future challenges.
Starting is the easiest part.
The problem won’t get easier with time. The first step is both the simplest and easiest. Put your foot on the path and start walking to the post quantum future.

