External Cryptographic Inventory.

Step 1 for Post-Quantum Cryptography Transition is Inventory: The Five Pillars of Cryptographic Discovery & Inventory.
In minutes. Continuously. Including auto‑generated CBOM outputs
Understand what encryption is visible externally from your infrastructure.
External Network Risk
The first pillar focuses on the External Network, which includes any encryption that is visible outside of the organization’s perimeter. This encompasses SSL/TLS certificates, digital signatures, and encrypted communication channels that interact with customers, partners, and external stakeholders.
External-facing Encryption
Failure to properly manage external encryption exposes organizations to a variety of risks. For instance, expired or misconfigured SSL certificates can allow attackers to intercept sensitive communications. Additionally, external-facing encryption is often the first line of defense against quantum-based attacks. Quantum adversaries will likely target weak encryption methods that protect externally accessible systems.
To address these risks, organizations must regularly audit their external encryption infrastructure.
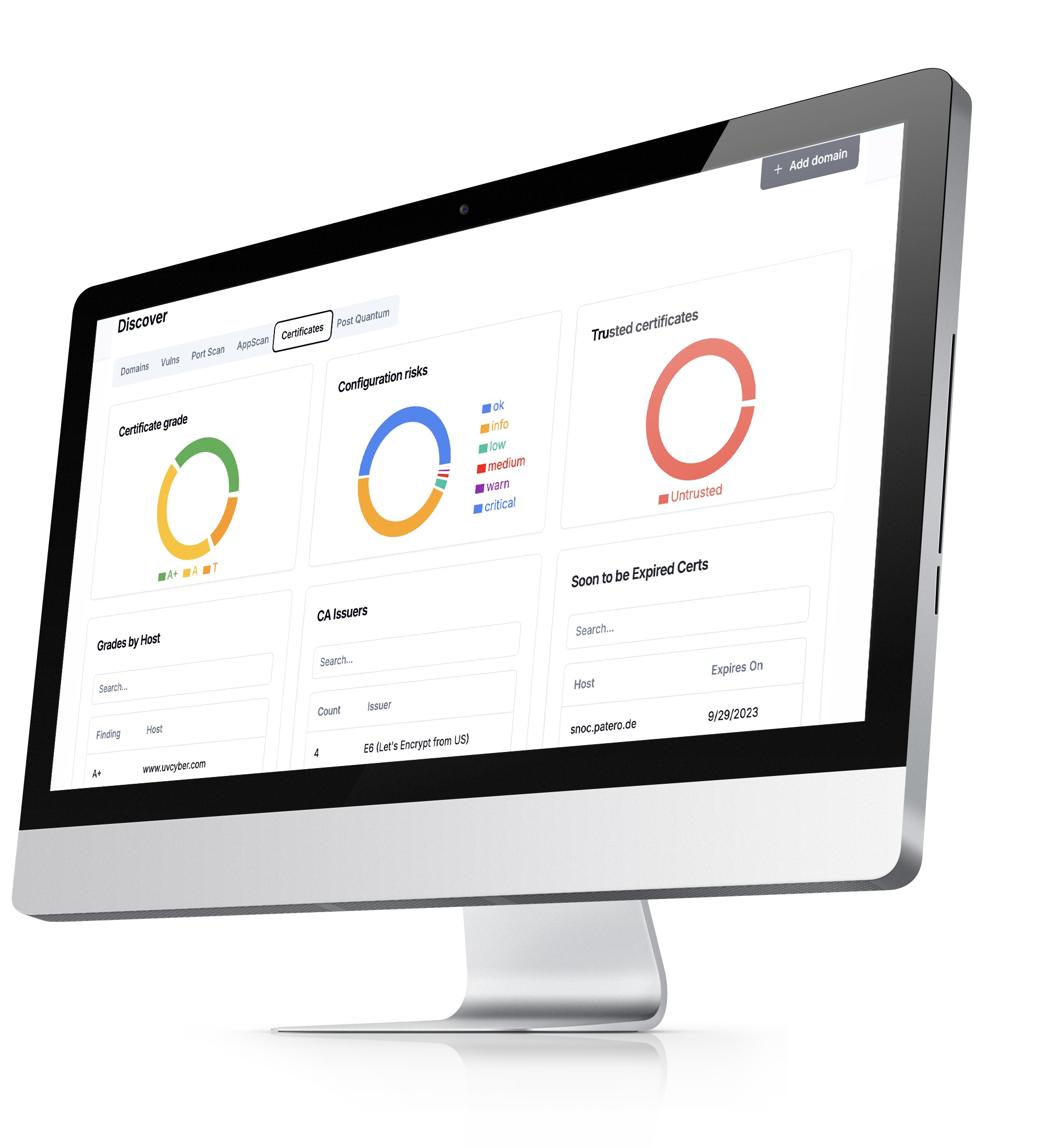
Discovering SSL/TLS certificates
Identify all certificates in use across websites, APIs, and email servers, ensuring that strong encryption algorithms (such as TLS 1.3) are employed.
01
Assessing cryptographic strength
Evaluate the strength of external cryptographic mechanisms in the context of post-quantum risks. Are there algorithms still relying on RSA or ECC? If so, these must be prioritized for upgrading to quantum-safe alternatives.
02
Inventory management
Ensure that all cryptographic assets, such as certificates and digital signatures, are properly inventoried and renewed before expiration.
03
QryptoCyber has an external-based scanner that automatically finds all externally-facing encryption
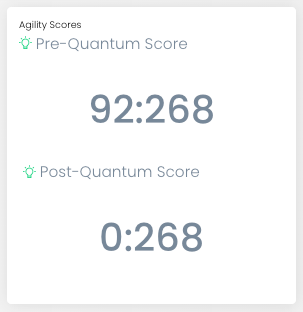
Then we immediately give you a both pre and post quantum risk profile. It’s really very simple.
How is This Possible?
Your encryption is already out there. You’re just not tracking it.
We do.
Let us tell you what you’re moving across the internet. We tell you what you have and what you need to fix.
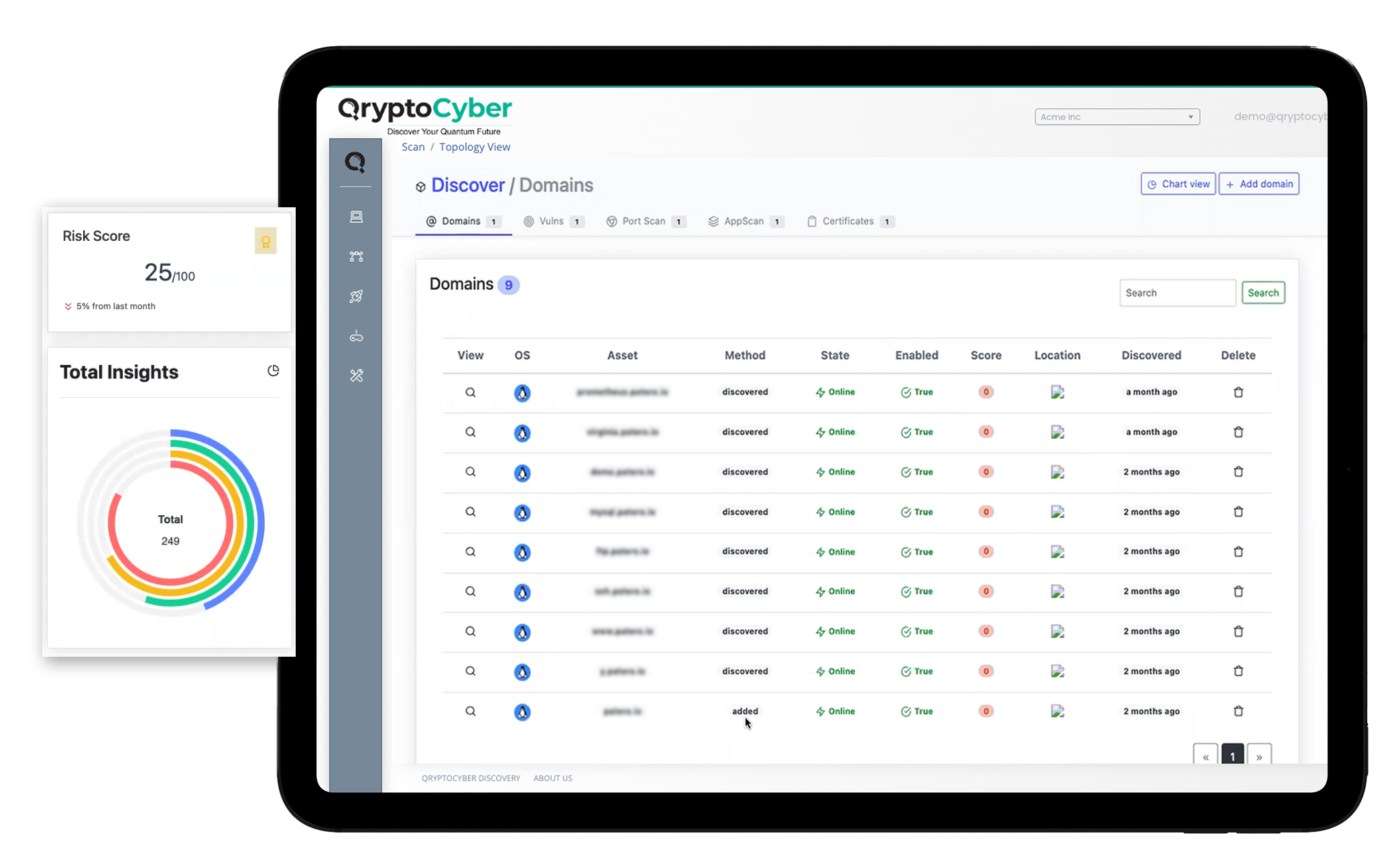
How do I Fix It?
QryptoCyber uses an inside out discovery tool that gives you complete encryption data on applications, databases, hardware… well everything.
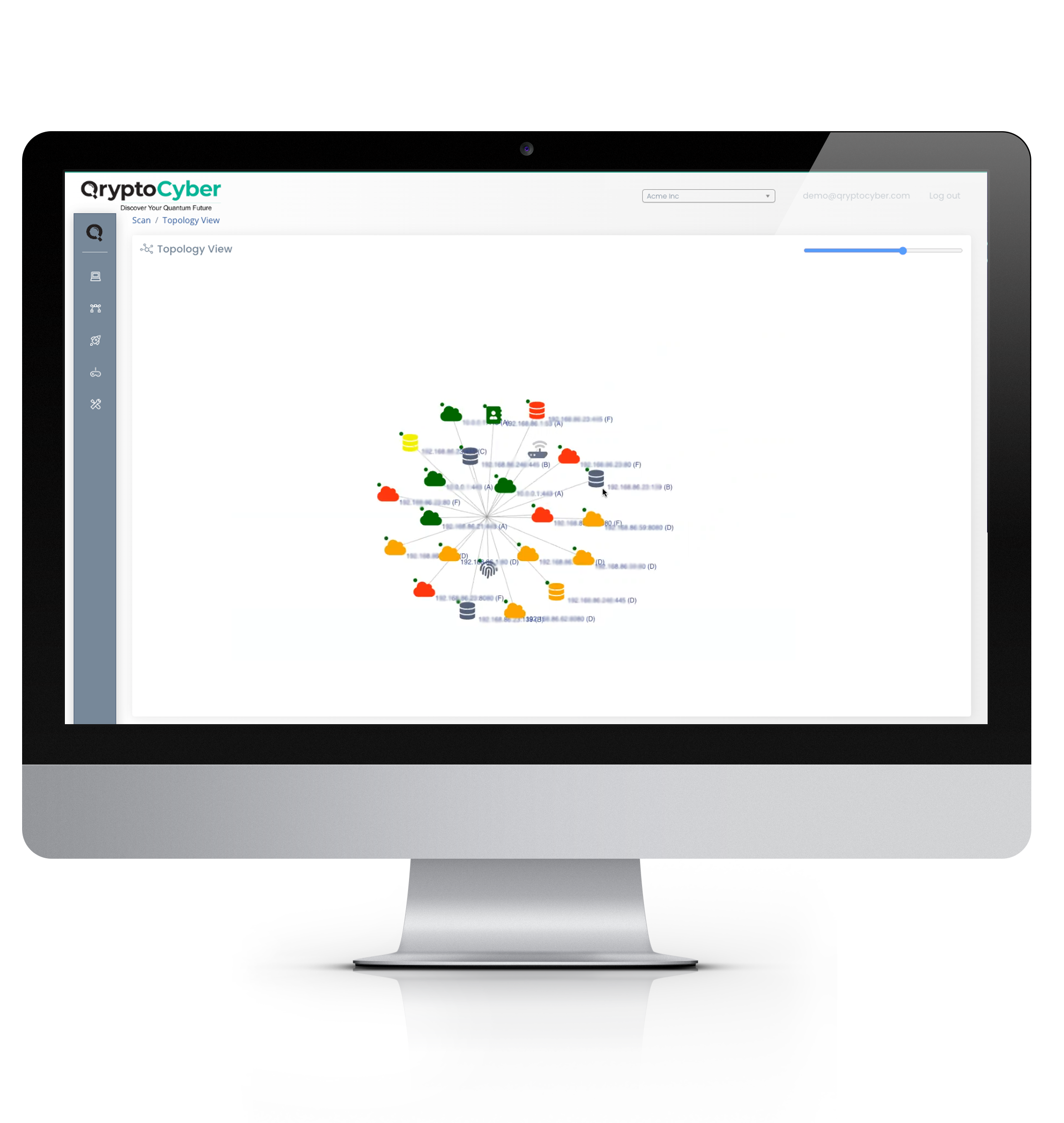
Replace Nothing. Gain Everything.
QryptoCyber is an additive technology stack that bolts onto your existing infrastructure.
Designed to add context… not complexity.
Starting is the easiest part.
The problem won’t get easier with time. The first step is both the simplest and easiest. Put your foot on the path and start walking to the post quantum future.

