Why QryptoCyber
The majority of organizations do not currently track what encryption standards are in use. We do for them.
We find encryption.
Cryptographic inventory identifies and assesses all cryptographic elements in an organization, providing essential visibility to prioritize the transition to post-quantum cryptography.
Many organizations lack visibility into their cryptographic assets, using varied encryption tools without centralized management, hindering assessment of their security against quantum risks.
QryptoCyber provides the only affordable, integrated PQC audit tool ready to fit seamlessly into your operations—making the process simple and effective
APPLICATION INTEGRATIONS







Simplifying the Journey
This isn’t just a quantum issue—it’s an IT and cybersecurity challenge.
01
Keep It Simple
QryptoCyber provides the only affordable, integrated PQC audit tool ready to fit seamlessly into your operations today
02
Keep It Reasonable
We’ve seen overly complex, costly products pitched for the post-quantum challenge. We offer effective, straightforward solutions—no exorbitant costs, no unnecessary complications
03
Keep It Fast
Your cryptographic inventory should be swift—completed in weeks. We can quickly gather data with internal agents or work with your existing tech for flexible deployment options.
04
Keep It Complete
Our Five Pillars framework ensures a complete cryptographic inventory. Updating only part of your encryption leaves gaps; a thorough approach is essential.
Stop Overthinking the Problem: Simplifying Your Post-Quantum Journey.
Hint: It’s Not a Quantum Problem.
Let’s Get This Done.
As we stand on the brink of a new era in cybersecurity, the shift to post-quantum cryptographic algorithms is on everyone’s mind. This transition is critical, but let’s not make it harder than it needs to be—especially when it comes to cryptographic inventory.
The release of new post-quantum algorithms means it’s time to take inventory now, not later.
Delaying this step only complicates the process and introduces unnecessary risk.
It’s crucial to understand that this isn’t a quantum problem—it’s an IT problem. While cybersecurity teams certainly play a vital role, the reality is that IT and infosec need to collaborate more closely than ever. This partnership is essential, yet often challenging on a day-to-day basis.
Building a comprehensive cryptographic inventory is a joint effort, and it’s one of the first steps toward securing your systems against quantum threats.
QryptoCyber 3.0
We Solve Cryptographic Inventory
Flexible Deployment
QryptoCyber supports commonly used agents for internal scans, offering flexibility based on customer requests
Automated CBOM
Gain full cryptographic visibility in weeks to manage vulnerabilities for post-quantum security risks
Quantum Risk Analysis
Quantitative Quantum Risk Analysis (QQR) delivers a data-driven, financial view of quantum vulnerabilities
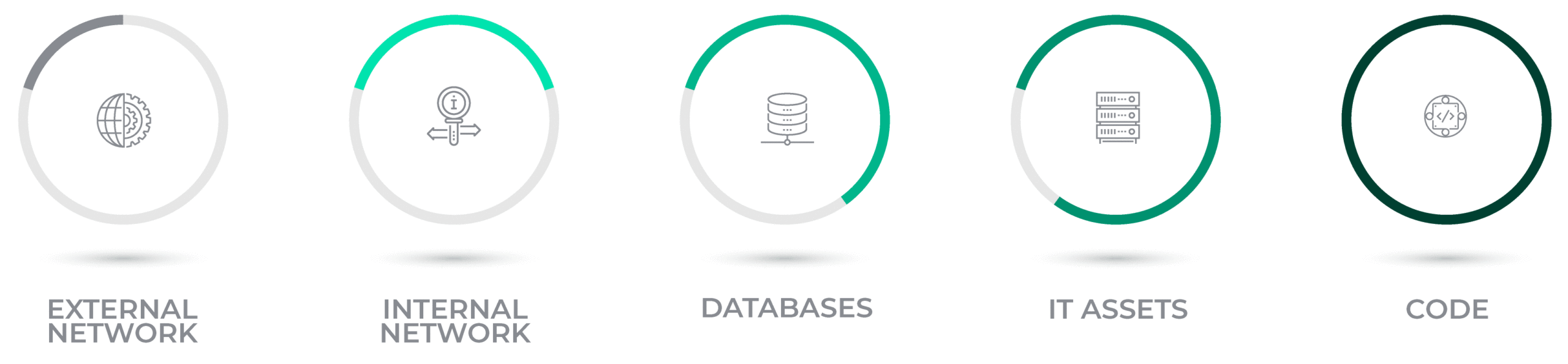
The five pillars of cryptographic discovery and inventory form the essential framework for identifying and securing an organization’s cryptographic footprint. By systematically assessing each area, organizations can prepare for quantum threats, reduce risk exposure, and ensure comprehensive visibility into their cryptographic landscape.

