COAR automates, orchestrates, and simplifies cryptographic inventory and CBOMs
Let’s be honest—encryption inventory and remediation shouldn’t feel like assembling IKEA furniture without instructions. That’s why we built COAR (Cryptographic Orchestration, Automation, and Remediation)—a smarter, faster way to track, fix, and manage your cryptographic assets before quantum computing turns your encryption into an open book.
Why COAR?
Because managing encryption shouldn’t be a guessing game. COAR automates, orchestrates, and simplifies cryptographic inventory and CBOMs, giving you the flexibility to:
- Find what you have – Scan your external and internal networks, IT assets, databases, and code.
- Map it out – Organize your cryptographic footprint into a usable, structured inventory.
- Fix it fast – Integrate with ticketing systems, remediation tools, and orchestration platforms.
- Move on with your life – Automate reporting, generate CBOMs, and ensure compliance without endless manual work.
This isn’t another bloated cybersecurity tool—it’s a solution that actually helps you get things done.

Cryptographic Orchestration That Works for You
Unlike static inventory tools that just spit out data, COAR is built for action. You don’t just collect encryption details—you do something with them.
- Custom Playbooks: Create automated workflows tailored to your security stack.
- Real-Time Post-Quantum Roadmap: Keep your cryptographic inventory up-to-date with live data.
- Flexible CBOM Management: Cut through the noise—segment and adjust CBOMs to match your needs.
Most CBOMs are a nightmare to manage, filled with data you don’t need and reports no one reads. COAR makes sure you get exactly what matters—nothing more, nothing less.
Find It. Roadmap It. Fix It. Forget It.
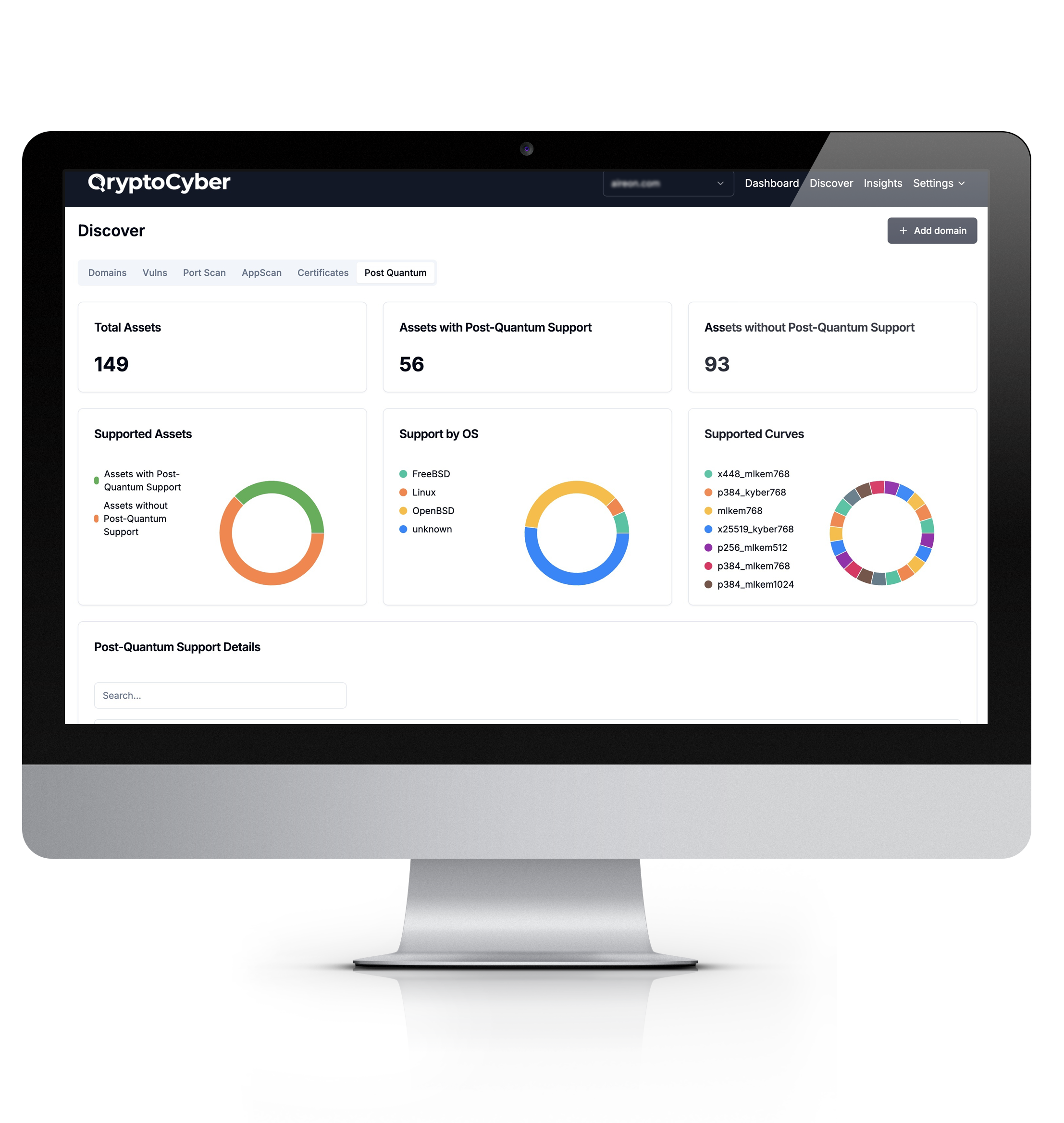
QryptoCyber isn’t just another scanner. It finds, categorizes, and analyzes encryption across your entire environment—so you know exactly what’s at risk.
Your cryptographic inventory can be delivered as:
- A Cryptographic Bill of Materials (CBOM)
- Structured data for automation and remediation
- Custom PDF reports for compliance and security teams
Run COAR as a SaaS solution or use our services—whatever works for you.
Why QryptoCyber? Because We Get It.
💡 BYOA (Bring Your Own Agent): You already have tools—we work with them. No extra installs, no vendor lock-in.
⚡ Weeks, Not Months: We’re not here to waste time. Your first inventory is done in three weeks, not six months.
🔗 100% API-Driven: Plug it into your existing workflows—no extra overhead, no unnecessary complexity.
No one has time for yet another security tool that adds more work instead of solving problems. COAR integrates directly into your existing ecosystem, giving you real-time insights and automated remediation without the hassle.
No Idea Where to Start? No Problem.
🔹 No installation needed – In most cases, we use what you already have.
🔹 CBOMs and reports built how YOU want them – Because compliance should be useful, not painful.
🔹 You control the data – Import, export, automate—whatever makes your life easier.
🔹 Orchestration means flexibility – Take action on findings using your tools and workflows.
You don’t need a six-month procurement nightmare for a three-week project. COAR keeps things simple—minimal risk, maximum impact.
About QryptoCyber
We help you stop guessing about encryption security. Post-quantum threats aren’t waiting, and neither should you.
✔️ Find & fix cryptographic vulnerabilities before they become real problems.
✔️ Map your cryptographic footprint to see what needs protection.
✔️ Transition to quantum-safe security before it’s too late.
Tired of scrambling to figure out your cryptographic risks? Let’s talk.