Cryptographic Inventory: The Nerdy Lifeguard Your Data Desperately Needs
Introduction
Alright, folks, let’s dive into the wild world of cryptographic inventory! Yes, it sounds like something only the biggest of nerds would care about. But guess what? If you don’t want your data floating around like a sad rubber ducky in the vast ocean of cyber threats, you’d better start caring too. So, buckle up and let’s see why cryptographic inventory is the unsung hero of your cybersecurity dreams.
What the Heck is Cryptographic Inventory?
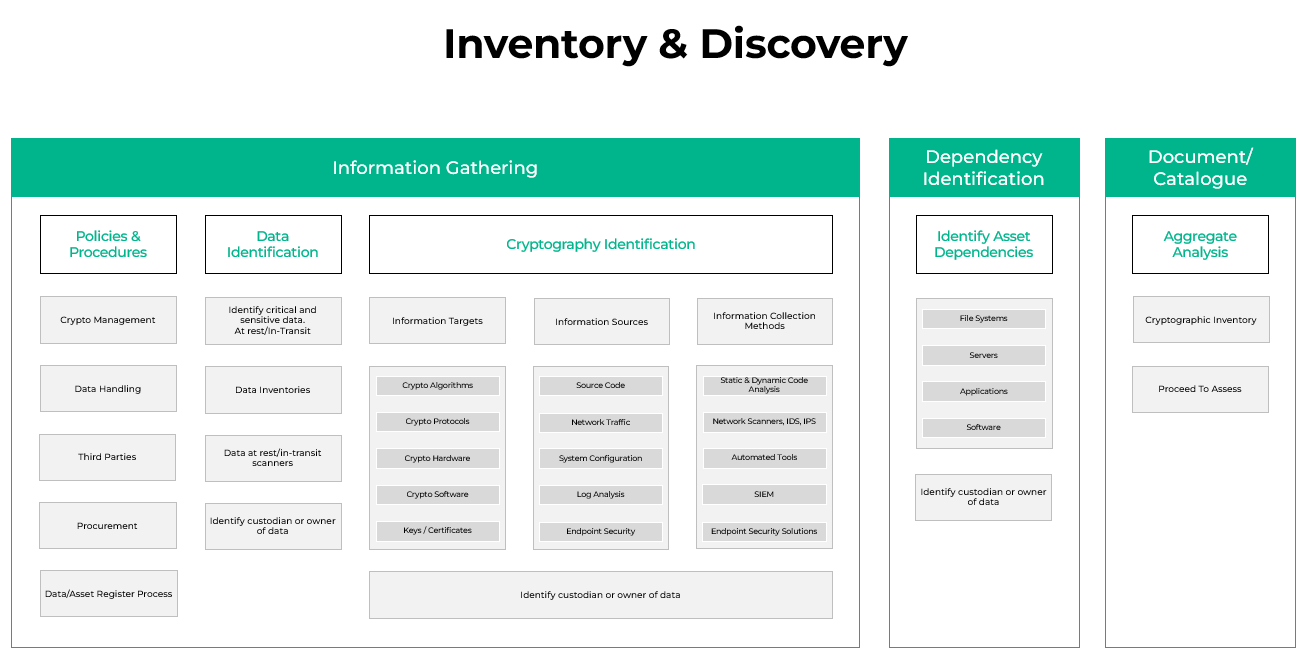
Imagine trying to find a single Lego piece in a room full of Legos. Now imagine those Legos are all your cryptographic assets – keys, certificates, algorithms, and more. Cryptographic inventory is like a meticulously organized Lego storage system. It’s a master list of every single cryptographic thingamajig your company uses. Without it, you’re just fumbling in the dark, hoping you grab the right piece while not stepping on one.
Why Should You Care?
- Visibility and Control: Think of it as your ultimate nerdy checklist. With a cryptographic inventory, you know exactly what you have, where it is, and whether it’s still useful. It’s like having X-ray vision for your security setup.
- Regulatory Compliance: Nobody likes getting a slap on the wrist from the compliance police. Keeping a detailed cryptographic inventory helps you avoid those awkward fines and the even more awkward conversations with your boss.
- Risk Management: Imagine still using Windows XP in 2024. Yikes, right? An outdated cryptographic setup is just as cringeworthy. Regularly updating your inventory means you can spot and fix vulnerabilities before they become headline news.
How to Build Your Nerdy Cryptographic Inventory
- Asset Identification: Start by listing every cryptographic asset you’ve got. Keys, certificates, algorithms – the whole shebang. Yes, it’s tedious. No, you can’t skip it.
- Assessment: Time to channel your inner critic. Evaluate each asset for its strength and relevance. If it’s outdated or weak, toss it in the bin (metaphorically, of course).
- Documentation: Write down every tiny detail. When it was created, what it’s used for, when it expires – the more info, the better. Think of it as writing a diary for your cryptographic assets.
- Continuous Monitoring: This isn’t a one-and-done deal. You’ve got to keep an eye on things, updating your inventory regularly. It’s like brushing your teeth – annoying but necessary.
Conclusion
So there you have it. Cryptographic inventory might sound as thrilling as watching paint dry, but it’s your best defense against cyber chaos. Get organized, stay updated, and keep your data safe from the digital boogeyman. Your future self will thank you.