Understanding Cryptographic Inventory: A Key to Quantum-Ready Security
Introduction
In the rapidly evolving world of cybersecurity, cryptographic inventory has become a cornerstone for organizations striving to achieve quantum readiness. As quantum computing advances, traditional encryption methods face significant threats. This blog will delve into the concept of cryptographic inventory, its importance, and how it prepares organizations for the quantum era.
What is Cryptographic Inventory?
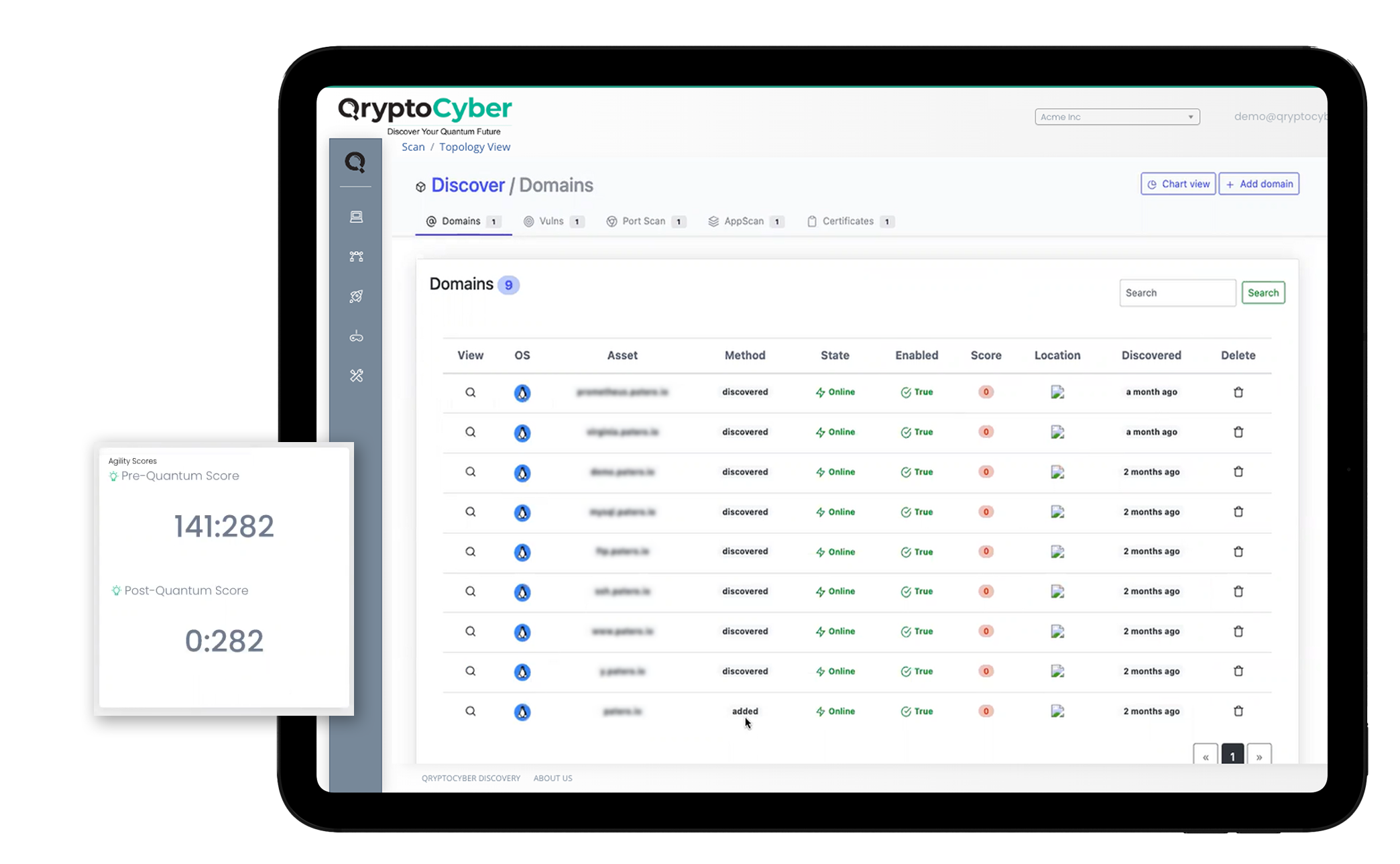
Cryptographic inventory is the systematic documentation and management of all cryptographic assets within an organization. This includes encryption algorithms, keys, certificates, and other cryptographic elements.
Why is Cryptographic Inventory Essential?
- Visibility and Control: Provides a comprehensive view of all cryptographic assets.
- Compliance: Ensures adherence to regulatory requirements and industry standards.
- Risk Management: Identifies vulnerabilities and mitigates risks associated with outdated or weak cryptographic methods.
Steps to Implement a Cryptographic Inventory
- Asset Identification: Catalog all cryptographic assets.
- Assessment: Evaluate the strength and relevance of each asset.
- Documentation: Maintain detailed records of cryptographic usage and updates.
- Monitoring: Continuously monitor and update the inventory.
Conclusion
Cryptographic inventory is not just a best practice but a necessity in the face of quantum computing. By implementing a robust cryptographic inventory, organizations can safeguard their data and ensure long-term security.