Understanding Cryptographic Inventory: A Cornerstone of Quantum-Ready Security
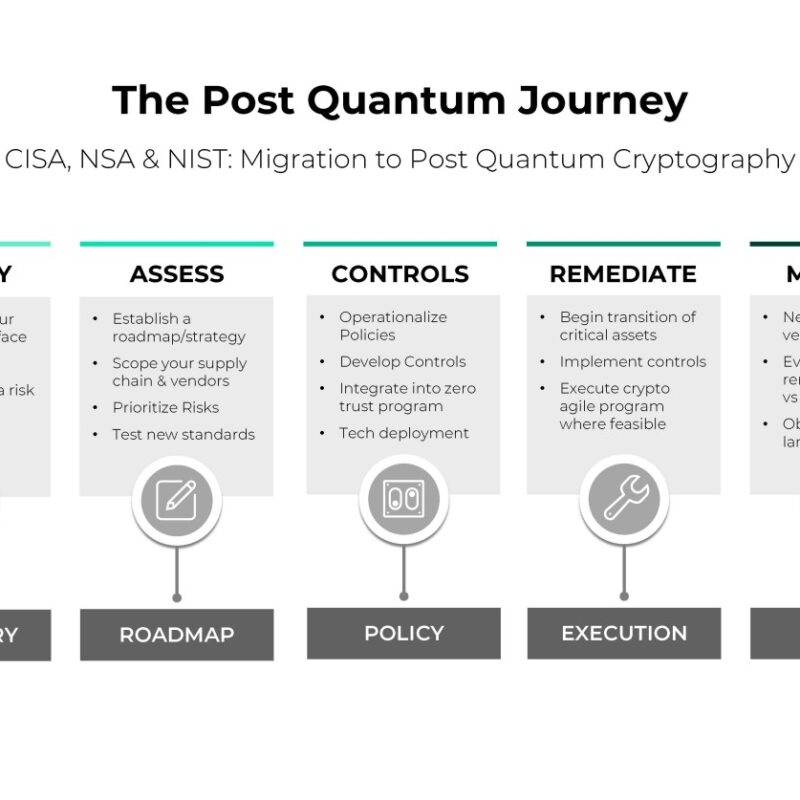
![The Post Quantum Journey CISA, NSA & NIST: Migration to Post Quantum Cryptography]()
Quantum Threat to RSA: The Impending End of RSA and Public Key Encryption
![Organizations must proactively prepare for the quantum era by adopting quantum-resistant encryption methods and updating their cryptographic policies.]()